Catch insider threats
no one else sees
When adversaries are on the inside, AI that understands normal operations becomes your best defense. Darktrace takes autonomous action to defend the full range of insider threat.

Insiders don’t need to break in
Resource hijacking
Insiders have been caught running unauthorized cryptocurrency mining operations within corporate environments, consuming IT resources and masking their activities
When credentials are clean, behavior tells the real story
Accelerate your investigations
10x
Darktrace's Cyber AI Analyst finds connections between isolated events and surfaces full security incidents, prioritized and contextualized. It has saved security teams the equivalent of up to 50,000 hours of investigation time per year.

From malicious intent to human error, stop the full spectrum of insider threats
Insider threats already have access, making them difficult to spot with tools that use attack data to find threats. Darktrace understands what is normal for every user and network entity, detecting subtle anomalies and alerting you to malicious or threatening activity that deviates from normal
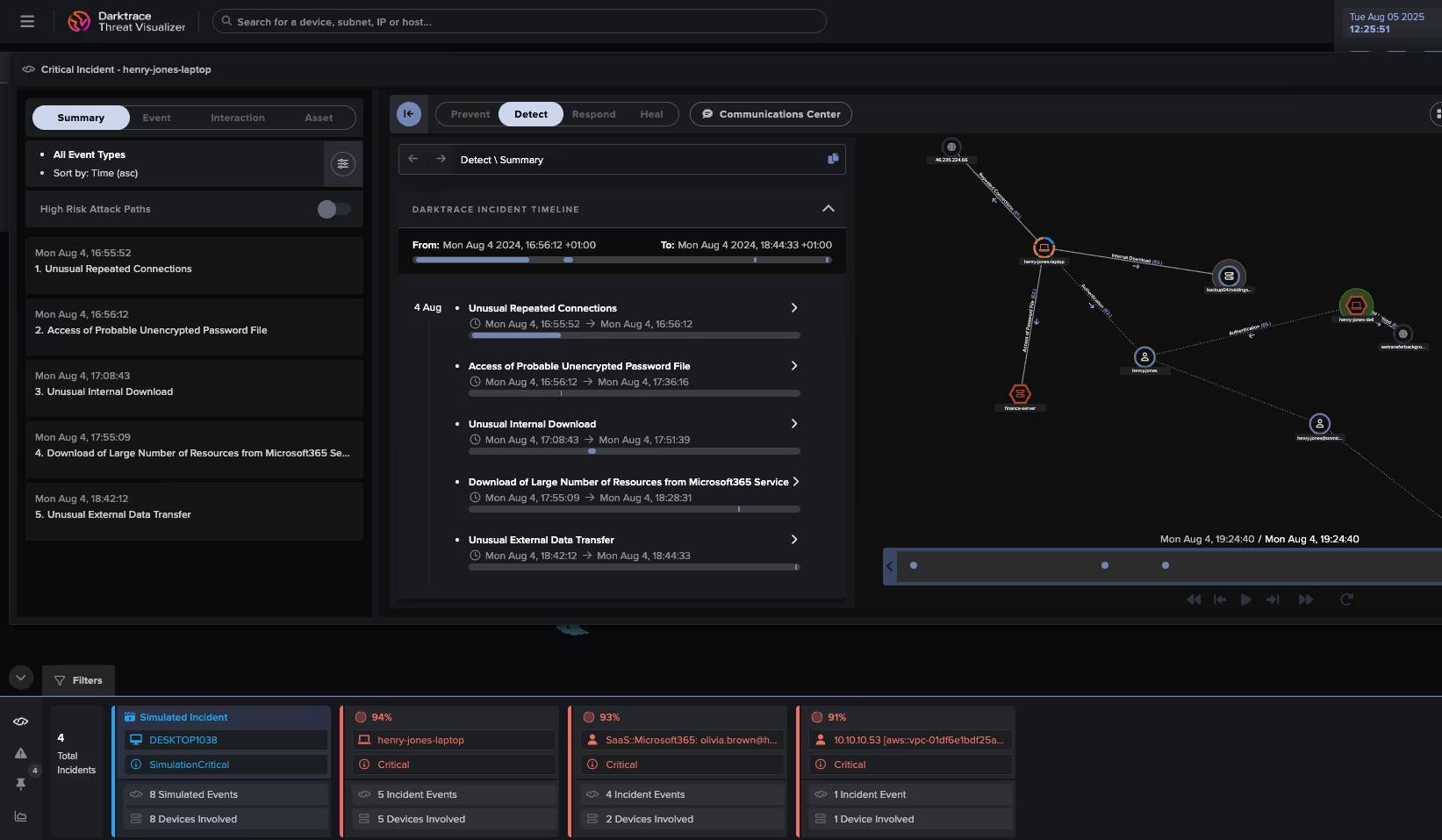
How Darktrace detected an insider threat that other tools missed
Initial compromise
An employee at a large manufacturing company connected a personal device to the corporate network and initiated unauthorized RDP connections to a rare external host. The organization’s firewall had predefined rules to block outbound RDP, but the attacker bypassed these controls by changing the destination port.
Darktrace’s AI detected the unusual activity and flagged the rogue device for investigation
Rule evasion and data exfiltration
By modifying the port used for RDP, the attacker circumvented firewall restrictions and maintained an active connection for over ten minutes. During this time, nearly 4MB of data was downloaded, representing a major deviation from normal network behavior.
Darktrace identified this anomaly as a potential exfiltration attempt and escalated the alert
Autonomous response
Darktrace’s AI determined the activity was threatening enough to warrant an immediate response. It autonomously blocked all outgoing traffic from the rogue device for ten minutes, preventing further data loss and giving the security team time to investigate.
This swift action stopped the unauthorized transfer before sensitive intellectual property could be exfiltrated
Insider threat confirmed
Upon investigation, the company discovered that the device belonged to an employee attempting to send valuable IP to a foreign competitor. Traditional security tools had failed to detect the threat due to their reliance on static rules, which the attacker had successfully bypassed.
Darktrace’s AI-based approach, which learns ‘normal’ behavior rather than relying on predefined rules, was able to detect and neutralize the insider threat in real time
Get ahead of insider threats
with continuous assessment of your most risky assets, attack path modeling and attack simulations
Simulate potential insider attacks
Darktrace attack engagements give teams the opportunity to test human risks with real phishing emails sent from internal accounts

Identify largest human risks
Understand cyber risk in an ongoing, real-world context that shows how attacks might progress and potential choke points in your people or technology

See your most at risk users
Discover your riskiest users and assets based on liability, access, and exposure, and then shore up defenses around them

Go beyond simple patch lists
Get prioritized mitigation steps paired with their potential risk outcomes, making it easier to take proactive steps toward greater resilience

Over 267 reviews on Gartner Peer Insights
Dive deeper
Explore our curated resources to gain deeper insights into the evolving landscape of insider threats and best practices for detection and response

Top 6 network security challenges
Explore critical challenges to securing today’s modern, integrated networks and how security teams can stay compliant in today's landscape.

Darktrace / NETWORK
Learn how Darktrace enables continuous visibility, real-time investigation, and autonomous response to contain threats before damage is done.

Insider threat truths
This blog explores the growing risk of insider threats in OT environments, highlighting real-world examples and limitations of traditional detection methods.
See Darktrace in action
Protect your organization from insider threats. See what Darktrace’s AI finds in your environment.
Cybersecurity for your whole business
Frequently asked questions
Yes, Darktrace can differentiate between malicious and accidental insider activity using its Self-Learning AI. It builds a baseline understanding of normal user behavior, so when activity deviates from this pattern, it can identify potential threats.
Malicious Insider Threats: These often involve deliberate actions like data theft, sabotage, or unauthorized access for personal gain.
Accidental Insider Threats: These might include sending sensitive data to the wrong recipient or misconfiguring access controls due to negligence.
While Darktrace may not always determine intent directly, it can infer risk levels based on the nature, context, and severity of the anomaly. For example, a user suddenly accessing sensitive files before resigning might be flagged as higher risk than someone who accidentally shares a document.
Darktrace’s Cyber AI Analyst runs continuous investigations on events, re-investigating existing alerts with emerging data to ensure thorough analysis. Each investigation produces detailed natural language summaries, providing security teams with clear decision logic and well-defined recommended actions to reduce false positives and speed up response efforts.
So, while Darktrace doesn't label actions as "malicious" or "accidental" per se, it provides the context and risk assessment needed for security teams to make that judgment.
Darktrace detects early signs of insider threats by continuously monitoring network and user behavior. The AI learns what is normal for each user, device, and service. Any deviation, such as a user accessing sensitive files they do not normally interact with or sending unusual amounts of data, is flagged as suspicious. By identifying subtle signs of malicious intent, Darktrace can detect threats before significant damage occurs. Autonomous Response functions also allow Darktrace to take action depending on the severity of the event to stop data loss all together.
Darktrace detects lateral movement or privilege escalation by monitoring patterns of behavior across the entire network. When an internal user attempts to move from one system or network segment to another, Darktrace can spot this lateral movement by analyzing unusual access patterns. Additionally, if a user’s privileges increase unexpectedly, such as gaining access to sensitive areas or systems they don’t typically use, Darktrace flags this behavior for investigation.
Darktrace is particularly effective at detecting insider threats in remote or shadow IT environments by monitoring network traffic and user behavior across both authorized and unauthorized systems. Even if an employee uses unsanctioned devices or connects to unauthorized cloud services, Darktrace can track these activities by analyzing unusual access patterns. The AI can detect non-compliant behaviors such as connecting to unauthorized apps or services, providing early alerts to the security team.
Yes, Darktrace can monitor the use of unsanctioned SaaS tools and personal devices connected to the network. Through its comprehensive behavioral analysis, it can detect when employees connect to or interact with unauthorized applications or devices. This includes monitoring network traffic, user access behavior, and the use of unsanctioned services. When an insider uses shadow IT or personal devices that are not authorized by the organization, Darktrace flags these activities as suspicious, enabling security teams to take action.




























