Threat Intelligence
Threat intelligence: How AI can help you protect your company
The continuing evolution of artificial intelligence technologies like machine learning, natural language processing, and advanced analytics can help cybercriminals develop new ways to trick their targets. In 2024, Security Affairs reported that 74% of security professionals said AI-powered cyber-threats have significantly impacted their organizations in some way.
When it comes to minimizing risk, companies need to fight fire with fire. Adopting an AI-powered threat intelligence solution can help your business future-proof its cybersecurity strategy and counter emerging AI-based threats.
This guide will explain how your company can use threat intelligence to enhance your cybersecurity posture and address evolving concerns.
How threat intelligence works
Threat intelligence is a cybersecurity tool that works by collecting data from various sources within your system and then conducting advanced analytics to produce actionable insights into your defenses.
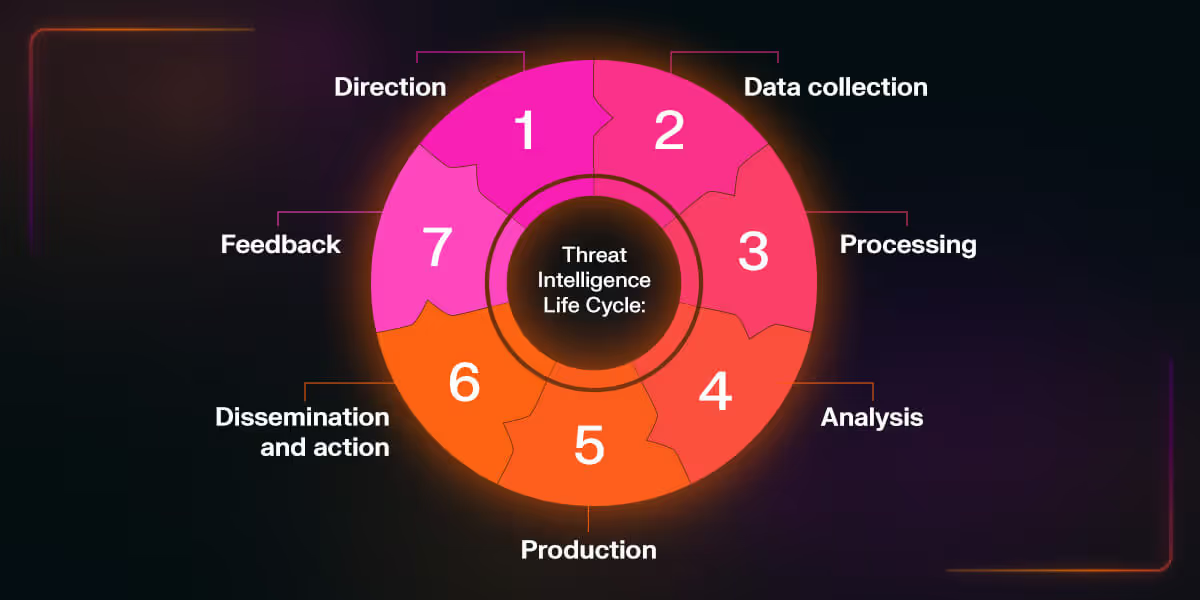
Here is a brief overview of the typical threat intelligence life cycle:
1. Direction
Also known as Discovery, this step involves assessing your internal controls and assets to shape your threat intelligence strategy. Key stakeholders in your organization will collaboratively define your goals and intended outcomes.
Based on this information, you can begin building out your strategy by:
- Prioritizing your most vulnerable assets
- Identifying the main threats these assets face
- Determining effective strategies for addressing these threats
- Identifying vulnerabilities within your systems
- The types of insight into these threats your organization needs
You can then choose to proceed by either investing in a new threat intelligence platform or developing one yourself.
2. Data collection
Your threat intelligence technology gathers data from various sources, including but not limited to:
- Social media platforms
- Open source intelligence (OSINT)
- Threat intelligence feeds
- Internal system logs
- Deep and dark websites
- Human intelligence (HUMINT)
It then compiles all that information into a data lake, a repository for large volumes of raw data, for the next step.
3. Processing
The system takes the raw data and processes it to make it readable for your analytics technology.
Data processing includes the following steps:
- Cleaning: The software identifies and corrects problematic data to ensure accurate analyses and remove errors.
- Filtering: The system removes all irrelevant data to ensure all insights extracted truly apply to your environment.
- Formatting: Your system will structure the raw data so it is readable by your threat intelligence platform. This step may involve standardizing date and time formats, aligning data types, or any other action that will make the data suitable for processing.
- Enriching: Some advanced systems will enrich the data by adding context, which makes it more useful for generating actionable insights.
4. Analysis
The AI-powered system then analyzes the cleaned and processed data to identify possible threats by flagging patterns and anomalies.
Artificial intelligence capabilities are important in this step because they can rapidly examine thousands of data points and identify relevant trends human analysts might miss.
Techniques commonly used for this step include but are not limited to:
- Statistical analysis
- Machine learning (ML)
- Data mining
Incorporating AI into these techniques makes it possible to run reports and analyses much faster than a human analyst could.
5. Production
The results of these analyses are then compiled into a threat intelligence report that details all identified threats and their potential impacts.
One of the most important components of this report is the recommended countermeasures, which sums up the best steps you and your stakeholders can take to defend against the identified threats.
6. Dissemination and action
The completed report is distributed to the intended recipients in a timely fashion to enable stakeholders to view and understand the data.
It's important to ensure each party receives the information that is relevant to them. For example, while your C-suite requires a higher-level overview of general intelligence insights, your operational technology (OT) and information technology (IT) teams will require more specific data points.
7. Feedback
Ongoing assessment and feedback are essential for gauging the effectiveness of your intelligence strategy. Collaboration is key for this step, as receiving feedback from your stakeholders can help you identify areas for improvement in future intelligence cycles.
Ultimately, the primary goal of this stage is to ensure your threat intelligence system is producing the best possible intelligence. Some important questions stakeholders should answer include:
- Are cyber-threat feeds providing sufficient data on new and evolving threats?
- How effective are your existing security controls in catching and eliminating threats?
- Are your analytics and reporting tools capable of generating actionable insights that help you anticipate potential threats as well as known ones?
Answering these questions and others will help your team identify possible opportunities for further improvement.
What data does threat intelligence collect?

Threat intelligence typically consists of any insights that could help your system learn how to identify and neutralize cyber-threats.
It's important to note the difference between information and intelligence here. Unlike raw information, intelligence gets processed and analyzed to enable you to extract valuable insights from it.
Some examples of the most important points of threat intelligence include:
- Indicators of compromise (IOCs): These are clear signs of a compromised system, such as IP addresses associated with malicious activity, specific file signatures, malware hashes, and phishing site URLs.
- Tactics, techniques, and procedures (TTPs): These data points include descriptive details on typical threat actors' operations, such as their patterns when moving within a network or specific tactics they use to gain entry into your system.
- Vulnerability data: A threat intelligence system will log and monitor important details regarding known weaknesses in your IT assets, which helps the system prioritize more vulnerable areas.
- Threat actor profiles: Your system will capture information on the people behind cyber-attacks, such as their known capabilities, past attacks, and most likely motivations.
- Event data: The system will extract event data from internal sources such as system logs, network traffic logs, and user activity logs.
Although this data may enter your threat intelligence system in any format, automated technologies can automatically format that information to make it compatible with your analytics tools. This step is critical for reducing errors and enhancing the specificity of the insights you gain.
Types of cyber-threat intelligence
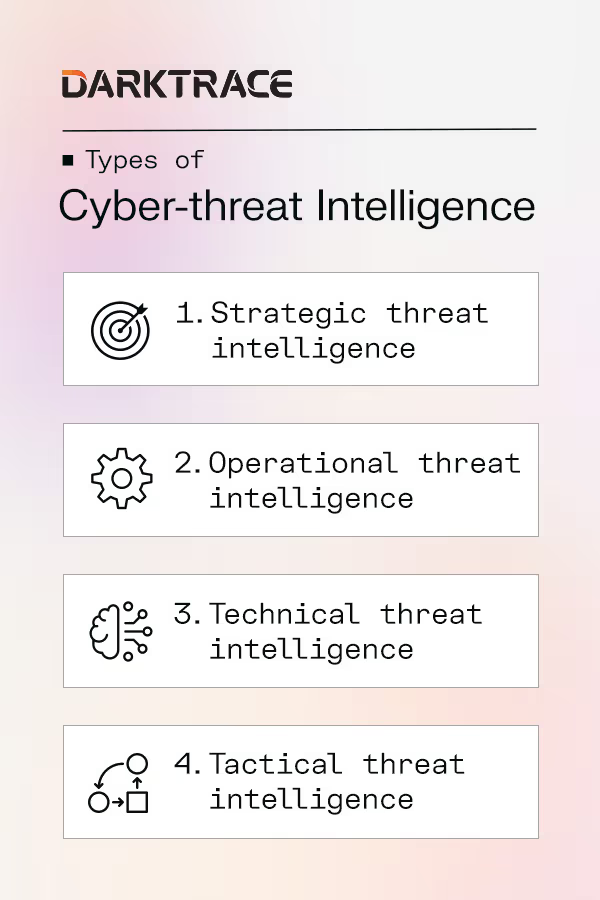
There are various types of threat intelligence your organization may use, each with distinct advantages and use cases.
The four different types of cyber intelligence include the following.
1. Strategic threat intelligence
C-suite executives and other company decision-makers benefit most from strategic threat intelligence, which offers nontechnical insights into high-level factors such as attacker motivations and the consequences of a breach.
This intelligence helps business leaders better inform security strategies such as:
- Resource allocation
- Policy development
- Process improvements
- Investment prioritization
2. Operational threat intelligence
Operational threat intelligence focuses on the personal elements of specific cyber operations or campaigns, such as:
- Attacker motivations
- Threat targets
- Common attack methods
- Attacker capabilities
- The nature and timing of attacks
Incident response teams rely on this information to gain a more complete understanding of an attack's context, which can help enhance the defense's effectiveness.
3. Technical threat intelligence
This type of threat intelligence homes in on clear indicators of compromise (IOCs), including:
- Malware samples
- Patterns in phishing message content
- Reported IP addresses
- Fraudulent URLs
Most of these IOCs become obsolete within a few days or weeks, so proactive identification and detection is critical for real-time defensive operations. Your threat intelligence system's ability to detect it triggers automated systems to neutralize the threat and notify security professionals of a potential breach.
4. Tactical threat intelligence
Tactical threat intelligence focuses on gaining insight into TTPs, the specific methods malicious actors use to carry out cyber-threats.
This data supplements strategic threat intelligence by providing granular real-time insights into threats as they evolve. Essentially, security analysts can use tactical threat intelligence to make the overall strategy more actionable and relevant to the environment's most significant threats.
Tactical intelligence is most useful for security analysts, as it provides valuable insights into the specific tools and techniques hackers might use to launch an attack.
The role of AI in the threat intelligence life cycle

In our State of AI Cybersecurity report for 2024, we found that 95% of cybersecurity professionals believe incorporating artificial intelligence into threat intelligence tools will help boost companies' defenses.
Further, the Department of Homeland Security (DHS) has stated that AI and ML technologies are advantageous in enhancing the nation's cybersecurity posture. The department's Science and Technology Directorate (S&T) is leading the charge on researching and implementing AI-powered tools in the national ecosystem.
Some of the most notable benefits of AI technologies in cybersecurity include:
- Detailed threat intelligence reports: An AI system that learns the context of typical operations in your business can produce insights identifying the highest-priority assets and threats.
- Accuracy and efficiency: AI can analyze and identify threats much faster and more accurately than human data analysts can, which increases efficiency, reduces false positives, and makes it easier to keep up with emerging threats.
- Enhanced threat detection: Artificial intelligence enables you to catch threats faster than with legacy cybersecurity tools and human professionals.
- Predictive analytics: One of the biggest benefits of AI is its ability to predict future events based on observable patterns in your system. This capability enables you to eliminate even zero-day threats without disrupting operations.
- Customized protocols: Machine learning capabilities enable an AI-powered threat intelligence platform to understand the normal operating context of your business, so it can more accurately react to abnormal behaviors.
- Continuous learning: AI is always learning, so you can count on an AI-powered cybersecurity program to continuously monitor and evaluate your tech stack for new threats.
Although it's still fairly new to the mainstream tech landscape, AI is shaping the future of cybersecurity and digital risk management.
Investing in threat intelligence tools
Your company needs to choose a platform that simplifies your tech stack via seamless integrations and data collection. An all-in-one cybersecurity solution with threat intelligence capabilities can help minimize errors by consolidating all your system information into one intuitive platform.
OT security threat intelligence should be handled with the same care and speed as IT-focused threat intelligence, and vice versa.
For example, Darktrace is a comprehensive AI-powered cybersecurity platform with advanced threat intelligence and elimination capabilities. Its integrated AI technologies are able to analyze and report on threats throughout your system, providing enhanced visibility into all areas.
With insight into all your organization's tech tools and solutions, you can gain greater control over your cybersecurity strategy. Plus, AI analytics and reporting capabilities provide more detailed information for key decision-makers in your company, allowing you to make better tech investment decisions at various levels of your organization.
What to look for in a threat intelligence platform
Features and capabilities of top threat intelligence platforms include but are not limited to:
- Real-time monitoring: An AI-powered platform that continuously inspects your system, identifies assets, and investigates alerts in real time can help you minimize your risk by catching anomalies faster than humans or legacy systems can.
- Seamless integration: Your system should pull data from all the components of your tech stack to gain complete visibility into your assets and identify incidents as soon as they occur.
- High containment time reduction: Leveraging a proactive approach to cybersecurity can reduce detection and reaction time by more than 90% with the right solution.
- Unified OT and IT operations: Your IT and OT professionals must work together to protect all the interconnected devices in your system, and a unified solution that can cover all those components from one location can significantly boost efficiency and reduce risk.
Darktrace threat detection examples
1. Detection of SmokeLoader Malware
Darktrace / NETWORK achieves enterprise ransomware protection that can detect and stop loader malware like SmokeLoader. In this customer’s case, our AI autonomously investigated suspicious network activity – relating seemingly isolated connections into a broader C2 incident – and alerted the security team.
2. Detection of Gootloader Malware
Cyber-attackers used Gootloader malware in an attempt to compromise the network of an American company. Gootloader can download additional malicious payloads, allowing threat actors to steal information or encrypt files for ransom.
Darktrace’s network security tools detected the unusual activity of the compromised device, including beaconing, SMB scanning, and downloading suspicious files. Using AI in cyber security allowed Darktrace to identify and neutralize Gootloader, protecting the company’s network.
Read the whole story on our blog


























