Intelligent cloud security powered by Self-Learning AI
Darktrace / CLOUD delivers complete cyber resilience for hybrid and multi-cloud environments

Rising complexity and
lack of visibility
Achieve cyber resilience with adaptive, intelligent AI built to secure your multi-cloud environment.

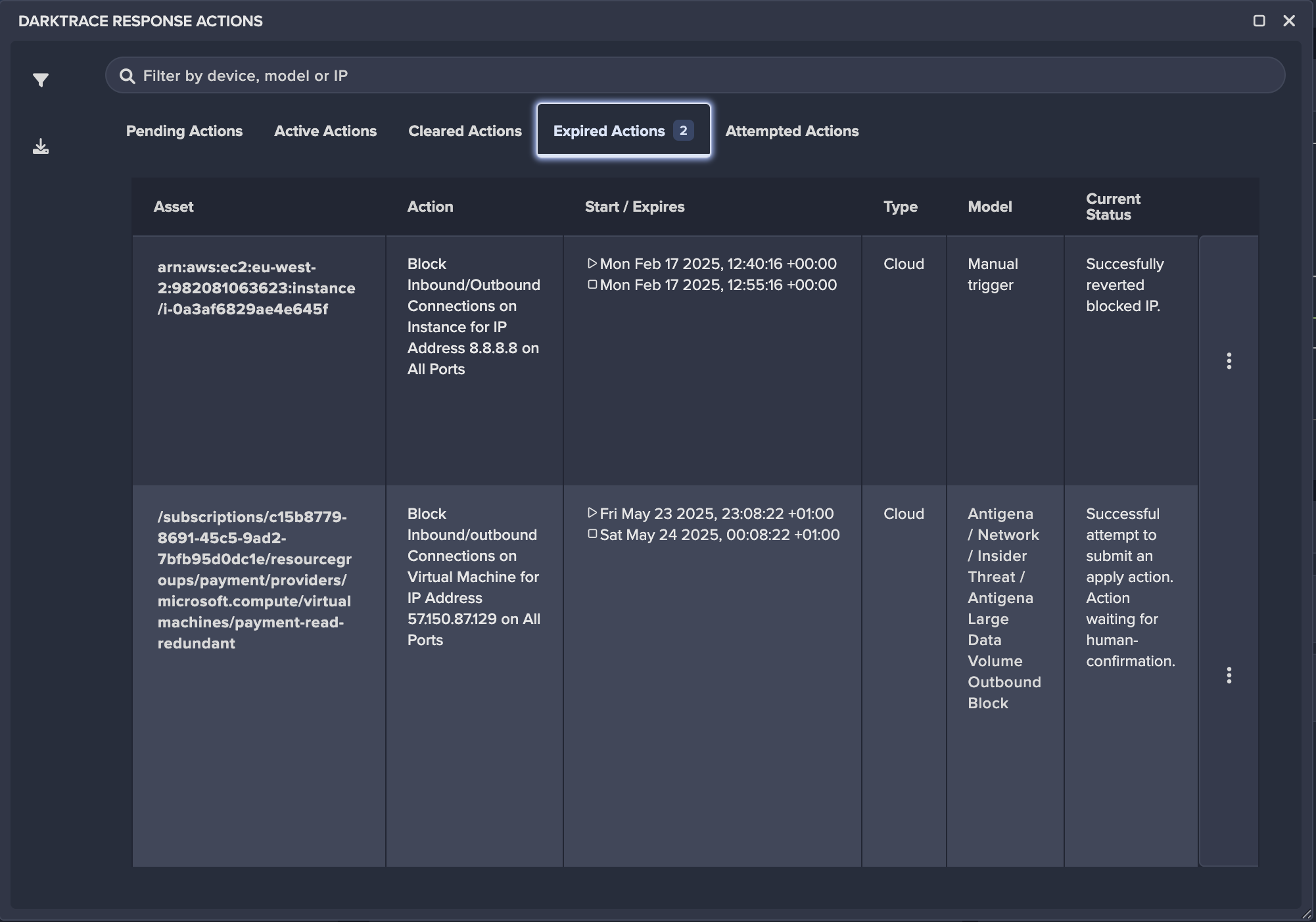
Disarm known and novel cloud-based threats quickly with platform-native response
Self-Learning AI™ continuously monitors activity across cloud assets, containers, APIs, and users correlated with detailed identity and network context to rapidly detect malicious activity
Cyber AI Analyst™ automatically triages every alert augmenting your human team, and Forensic Acquisition & Investigation offers unmatched forensic depth
Platform-native Autonomous Response neutralizes malicious activity with surgical accuracy while preventing disruption to cloud infrastructure or service
Evaluate in your environment today




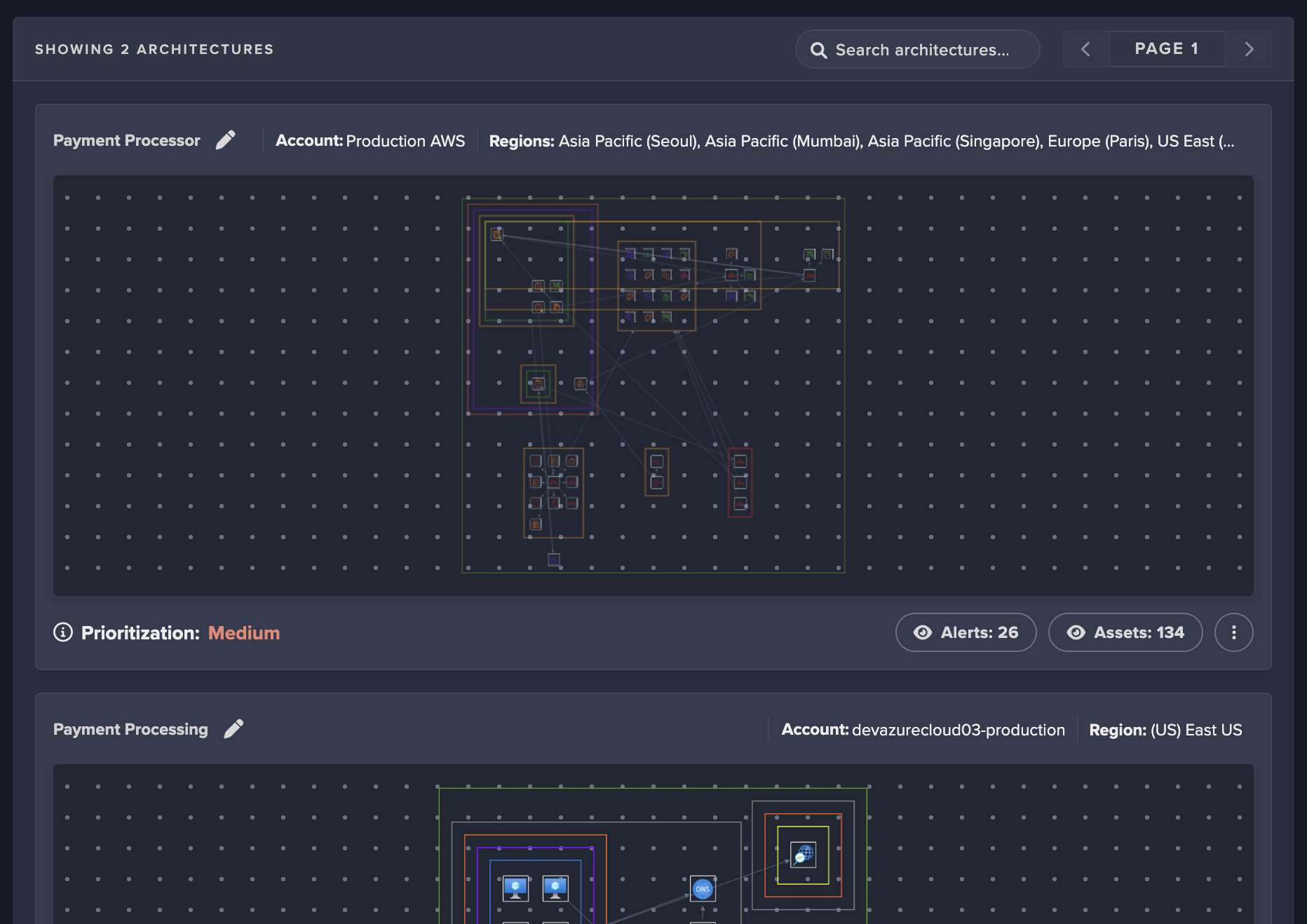
Understand your complex cloud footprint
Achieve real-time visibility into all cloud assets and architectures with speed, flexibility, and scale across hybrid, multi-cloud environments.
with the industry’s only dynamic, real-time architecture that brings unparalleled insight and rapid threat response to your cloud assets, delivering a clear picture of your infrastructure that changes as your infrastructure evolves to display live detection information
at scale in containerized environments such as Kubernetes. Continuously analyze network traffic within clusters against a deep understanding of your business to inform dynamic, real-time actions and ensure cyber resilience within the cloud
across on-premises and cloud environments to secure and accelerate your cloud migration journey. Seamlessly extend existing workflows to the cloud and enable teams to collaborate with real-time visibility into asset utilization, cloud architecture, and access rights
Read the
solution brief
Discover how one customer saw an 85% ROI improvement in prevented data breaches and improved downtime

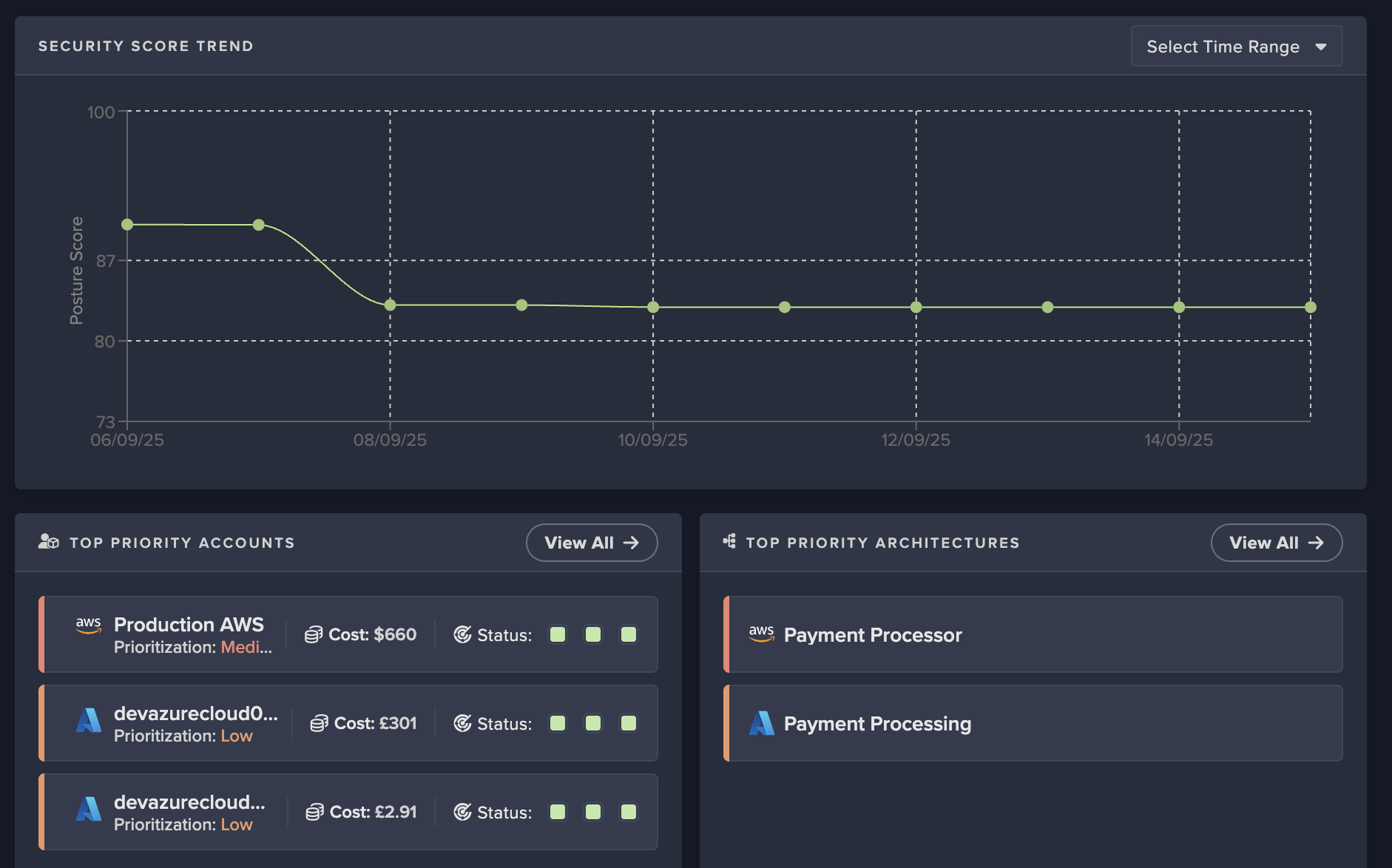
Prioritize your biggest risks based on a deep understanding of your unique business context
Protect against insider threats and lateral movement by prioritizating misconfigurations, ensuring the right role permissions and access, and shifting security operations from reactive to proactive to stay ahead of attacks.
Get a clear view of all identities, roles, and permissions within your cloud infrastructure to stop insider threats and lateral movement.
Top rankings and risk baselines provide an effective, prioritized view for cyber risk discovery and allow you to address the users, devices and vulnerabilities which pose the most severe compromise risk to your business.
Continuous learning of cyber risk is fed into the detection and response capabilities of the Darktrace ActiveAI Security Platform. Quickly evaluate the potential impact to affected assets during incidents and strengthen response along your most critical attack paths.
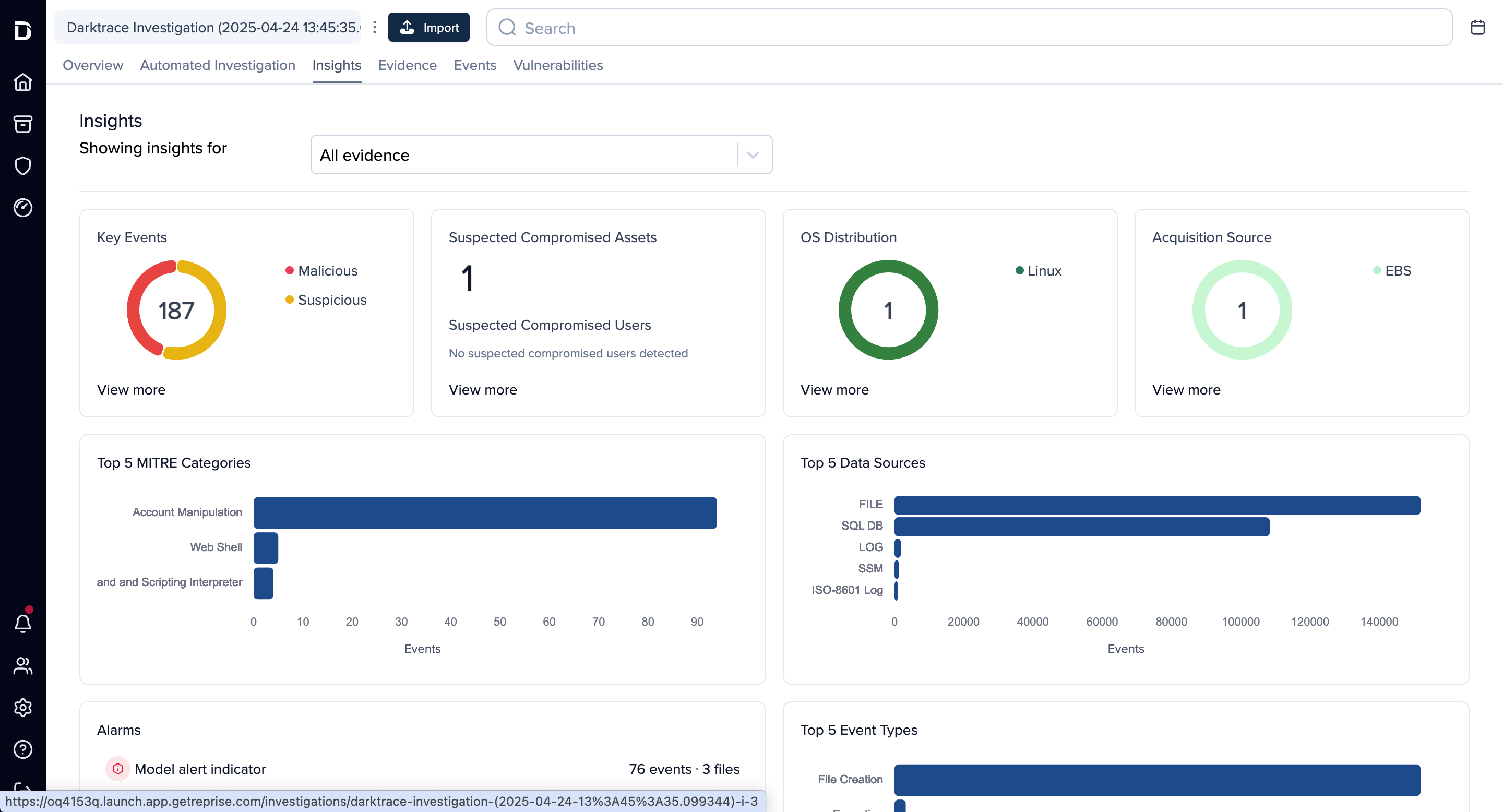
The industry’s first truly automated cloud forensics solution
Get forensic data – disks, memory, logs – directly from cloud services via secure APIs. No more opening tickets, chasing infrastructure, manually configuring snapshots, and missing time-sensitive workloads.
Immediately captures evidence and get interactive timelines that reconstructs attacker behavior. Get root cause analysis for cloud security alerts without combing through logs or artifacts manually.
Integrates with any alert source and deploys via API across regions, enabling fast, low-overhead response within existing workflows.
Quick & easy deployment with granularity where you need it
Deploys from the cloud in minutes
Data drawn either from lightweight host-based server agents or a combination of traffic mirroring and API logs
Supports multi-tenant, hybrid, and serverless environments






































