Security analysts investigate threats by finding patterns, forming hypotheses, reaching conclusions, and sharing their findings with the rest of the business. These are labor-intensive steps that take not only time, but years of training and expertise. And as operational technology (OT) becomes further integrated with the corporate network, and as threat-actors continue to advance their methods of attack, the emergence of a cyber security skills gap in the OT world becomes more and more evident.
The trend towards interconnected IT and OT environments is matched in equal measure by converging security teams. CISOs have assumed responsibility for the security of ICS environments without necessarily possessing specialized OT skills. Similarly, OT engineers are often handed security roles involving IT without sufficient training. As a result, a knowledge gap is emerging, with organizations struggling to find experts with the necessary skills in both operational technology and traditional IT.
However, developments in artificial intelligence are being leveraged to fill this skills shortage, and technology exists today that can stitch together related security events across OT and IT into a single incident — generating a meaningful, natural-language summary of the suspicious activity.
Darktrace’s Cyber AI Analyst for OT combines the skill of human expertise with the speed and scale of AI, empowering it to conduct expert investigations into hundreds of parallel threads simultaneously. This groundbreaking technology is the result of over 3 years of research and development at Darktrace’s R&D Center in Cambridge, UK — harnessing supervised machine learning to replicate the actions of expert OT and IT analysts. Every time a security alert is triggered, Cyber AI Analyst automatically pulls together a full incident report, drawing upon multiple related alerts and useful surrounding context to complete the picture.
Cyber AI Analyst for OT has domain knowledge from both OT and IT “baked in” to ensure that it can do a lot of the interpretation. An IT SOC can receive the specialized and detailed OT information relating to an incident, but also the higher-level abstractions and meaning to help them triage. Equally, OT engineers can, for example, be presented with a complete timeline of a zero-day ransomware infection as it emerges, without needing to know how to investigate file-sharing activity or command and control beaconing. Cyber AI Analyst for OT therefore not only saves security teams crucial time, but bridges the skills gap that increasingly widens as OT and IT environments continue to converge.
Investigating a ‘Triton 2.0’ attack
Cyber AI Analyst presents its findings in Darktrace’s graphical user interface, the Threat Visualizer. We can view an example of this by looking at a Triton-style cyber-attack captured within a customer environment.
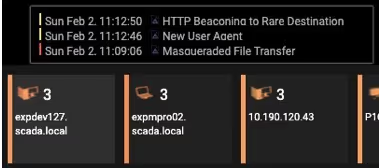
Figure 1: Three models are breached by a desktop device
The threat tray above shows three individual alerts pertaining to a particular device — expdev127.scada.local, a desktop belonging to a domain administrator. Working in real time in the background, Cyber AI Analyst for OT now stitches together these multiple alerts into a single security incident, and then surfaces this incident in a high-level narrative, displaying all stages of the attack lifecycle on a single timeline.
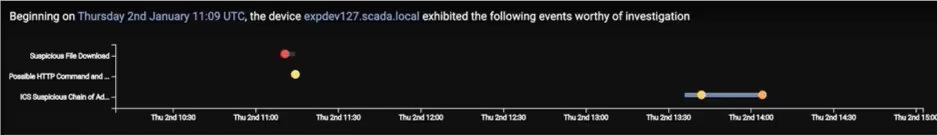
Figure 2: The Threat Visualizer surfaces a timeline of the suspicious events
We can see that over the span of three hours, Darktrace identified a suspicious file download, possible command and control traffic, and a chain of administrative connections it deemed worthy of investigation. The Threat Visualizer then surfaced this series of suspicious connections, showing how the malware penetrated from the upper parts of the control system through to a workstation that can interact with PLCs.

Figure 3: A graphical representation of the RDP communication
Since the initial compromise infected a domain administrator’s desktop, the primary ‘hop’ of remote desktop to the local domain controller illustrated here is not unusual at all — the usage of legitimate administrative RDP credentials is commonplace from this device. However, as the incident unfolds, Cyber AI Analyst subsequently recognizes that this is related to more suspicious events, and is able to go back and include these events in a single narrative.
The malware then makes a second hop — also via RDP — to an engineering workstation and finally reprograms a related PLC, all the while retaining the remote access chain. As with the Triton attack that targeted various power plants in 2017, this attack relied on commonplace administration sessions to transfer tools, and for remote command/program execution. The Threat Visualizer shows us the destination port, as well as the application protocol used to deliver the final stage of the attack.
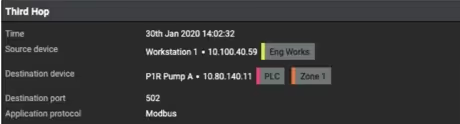
Figure 4: Further details of the reprogramming
Cyber AI Analyst converts the initial alerts into this incident report in real time, and the security team enter the fray armed with a much clearer and broader description of the incident, far sooner than if they had needed to perform these steps themselves. In this case, Cyber AI Analyst eventually includes seven alerts of different suspicious activities within this one incident, as well as multiple details that did not create alerts themselves but are strongly related and could have been omitted by an inexperienced analyst.
The near future of ICS attacks
Cyber-attacks on ICS are continuously evolving, with adversaries using the latest open-source technologies to launch evasive and machine-speed campaigns globally. While many organizations are turning to AI to face the scale, complexity, and speed of the cyber-threats they face in their IT and OT environments, we can also expect that these threat-actors will also start to use AI to achieve their objectives.
The threat-actors behind Triton blended mainstream IT attack techniques with specialized OT payloads and backed both up with strong operational discipline. The future addition of AI into such malware will allow it to achieve more inside a target network without persistent human oversight — and therefore dramatically decrease its chances of detection.
By combining both IT and OT analyst domain knowledge whilst operating at machine speed with a computer’s unwavering attention to detail, Cyber AI Analyst for OT will prove crucial for security teams by saving them vital time and filling in for any gaps in domain knowledge.






































