What is CTEM?
Continuous threat exposure management (CTEM) is a vital cybersecurity solution that mitigates risks posed by modern threat actors. This approach prioritizes potential risks, focusing on the most important vulnerabilities rather than trying to manage every gap. Advanced software, automation, and clear team collaboration are essential for implementing a successful CTEM strategy.
CTEM is a continuous, five-stage framework that can help your organization keep up with rapidly changing attack surfaces. Unlike Vulnerability Management (VM), which fixes lists of bugs, CTEM manages business risk. The core philosophy of CTEM is the importance of addressing risks based on exploitability and potential business impact. CTEM is more than a single tool or technology — it's a system that can significantly reduce breaches by focusing on validation over volume.
Why modern security teams need a CTEM cybersecurity strategy
Traditional patch cycles cannot react to the new vulnerabilities that cyber criminals exploit. CTEM offers a proactive solution that continuously assesses, validates, and reduces your organization’s exposure to business risks that evolving adversary tactics present.
The five stages of the CTEM cycle
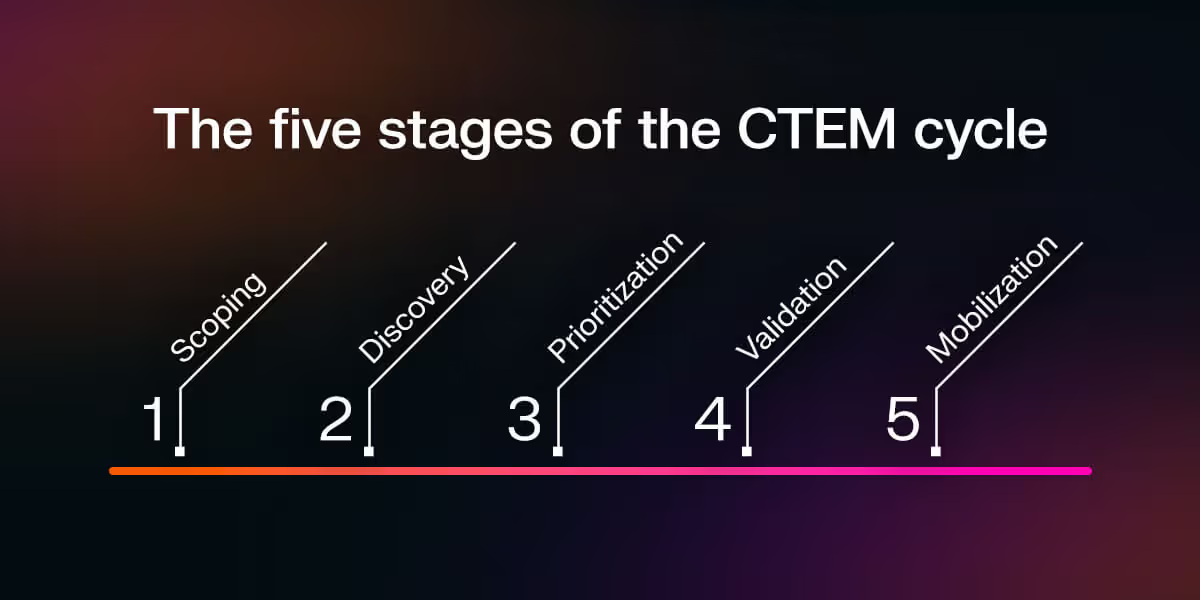
The CTEM cycle encompasses the following stages:
Stage 1: Scoping
Scoping involves identifying the most important elements to protect, such as critical assets, SaaS apps, and intellectual property. Personalizing your organization's CTEM parameters and objectives is essential, as this step defines the boundaries for the rest of the cycle.
First, you must determine which assets and systems to include and which ones take priority. These decisions are based on your company's threat environment and business objectives, so it's important to identify both what is most valuable and most vulnerable. Classify priority assets according to common threat categories:
- Unintentional external risks originating from human error, third-party vendor mistakes, and negligence
- Unintentional internal risks present within your internal departments
- Malicious external risks like criminal syndicates, threat actors, and nation-states
- Malicious internal risks arising from third-party vendors or rogue employees who may commit data theft
The most efficient way to prioritize assets is to quantify gaps in coverage and potential risks.
Stage 2: Discovery
During the second phase, you reveal assets beyond your organization's known inventory, such as forgotten APIs, shadow IT, and misconfigured clouds. Business, security, and IT teams benefit from collaboration when reviewing assets from the scoping phase and assessing their risk vulnerabilities, as working in concert better equips them to highlight and address information gaps.
Discovery should be a continuous process, not a quarterly scan. External Attack Surface Management (EASM) plays an important role in this process because it helps your team identify gaps and risks such as the following:
- Misconfigurations
- Third-party partner operations
- Weak credentials
- Expired certificates
- Excessively permissive identities
- Exposed code repositories
- Exposed domains
- Social media accounts
Stage 3: Prioritization
The prioritization phase maximizes defense by shifting from a focus on severity to a focus on risk likelihood and impact. Immediately address issues that are actively exploitable or located on critical paths.
While it's impossible to address every gap, CTEM helps narrow thousands of vulnerabilities down to a select handful that truly matter. Real-time risk prioritization enhances security and efficiency, helping your teams get ahead of cybersecurity threats. This systemic approach continuously reevaluates challenges based on urgency, compensating controls, and the value of targeting assets. During this phase, your goal is to answer the following critical questions:
- How do attackers use exposure gaps to move laterally through your system, and how quickly can they access valuable assets?
- How — and how rapidly — do your personnel and security controls detect and stop attacks?
- Which vulnerabilities present the greatest risk to your business operations?
The knowledge you gain from objective assessments during this stage helps inform your strategy and focus your security team's efforts on what matters most at a given point.
Stage 4: Validation
Validation involves testing your processes, controls, and procedures to ensure your security posture can stop predicted threats. Continuous attack simulations and evaluations within the CTEM cycle help identify the following:
- Specific ways a potential attacker could exploit exposures
- How well your control and monitoring systems mitigate threats
- The best treatments to improve security without disrupting your departments' operations
- The effectiveness of your security posture following remediation
It's important to keep your specific risks in context as you approach this stage, since validated ones inherently take precedence over those that are only theoretical.
A CTEM program might include validation methods such as EASM, digital risk protection service, and penetration testing. Technologies such as Exploit Prediction Assessment can also help automate this testing, making your processes more efficient.
Validation further supports your investment strategies. During this phase, your team can recreate real-world threats and situations such as business email compromise and phishing campaigns to evaluate how users react and which tools or education programs offer the most value.
Stage 5: Mobilization
Mobilization fixes your organization's cybersecurity processes. Remediation can include mitigation or acceptance, not just applying a patch. This phase requires clear communication and collaboration to reduce threat exposure, allowing IT and security teams to agree on what to fix and why. Focus on actions like:
- Continuously updating software
- Conducting scheduled security scans
- Training employees on the latest best practices
- Performing ongoing testing and validation
Moving from vulnerability management to exposure management
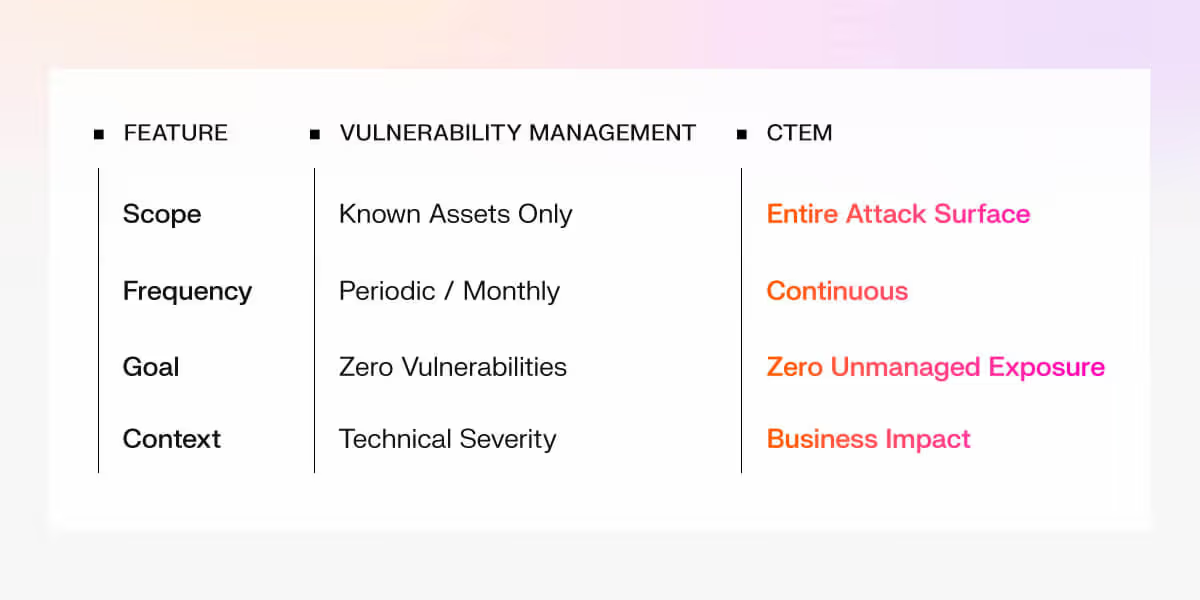
CTEM is a significant advancement from basic vulnerability management, enhancing cybersecurity in the following categories:
- Scope: While the VM strategy focuses on known assets, CTEM broadens the scope to include an organization's entire attack surface.
- Frequency: CTEM increases the frequency of traditional vulnerability management, taking periodic or monthly management to continuous management to enable ongoing defense-hardening in dynamic threat environments.
- Goal: The goal of VM is to achieve zero vulnerabilities, while the goal of CTEM is to achieve zero unmanaged exposure.
- Context: VM targets vulnerabilities based on technical severity. CTEM offers a more beneficial approach by targeting the vulnerabilities that have the greatest business impact.
The role of artificial intelligence in scaling CTEM
Humans cannot manually execute the CTEM cycle at speed. AI technology automates the discovery of hidden assets and the validation of complex attack paths. AI can predict which vulnerabilities cyber attackers are most likely to exploit next, helping security teams identify the most important risks without extra time and effort. Proactive AI-powered security tools operate as the brain that makes the CTEM framework feasible for lean teams.
Learn more about building a proactive CTEM security posture
Shifting from reactive damage control to proactive exposure management is crucial to hardening your defenses against evolving attack techniques. A mature CTEM program transforms security from a blocker into a business enabler. Explore Darktrace's research on Proactive Exposure Management and Attack Surface Management™ solutions.



























