What is National Institute of Standards and Technology (NIST)?
What is NIST?
The National Institute of Standards and Technology (NIST) is the federal technology agency that develops and promotes measurement standards, calibration services, and quality assurance programs critical to U.S. innovation and industrial competitiveness. Established in 1901, NIST operates as a nonregulatory agency within the U.S. Department of Commerce, advancing measurement science, standards, and technology to support economic security and improve quality of life.
NIST is the architect of fundamental security frameworks that shape how organizations worldwide approach risk management, threat detection, and incident response. Understanding NIST's methodologies and frameworks is essential for security teams navigating an increasingly complex threat landscape, where statistics show that 600 million attacks happen daily.
Why NIST matters in cybersecurity and risk management

NIST's mission is to promote innovation and industrial competitiveness through comprehensive standards, guidelines, and best practices that organizations can adapt to their needs. Organizations leverage NIST standards for several benefits:
- Improved security posture: NIST frameworks provide structured approaches that help organizations identify and address vulnerabilities before adversaries exploit them. The frameworks encourage prioritization based on risk impact and likelihood, ensuring that security investments align with business objectives and real-world threat profiles.
- Common language across stakeholders: These guidelines create a shared vocabulary that enables clear communication between technical teams, executives, vendors, and partners. This common understanding accelerates decision-making, reduces miscommunication during incident response, and ensures alignment on cybersecurity protocols and goals between all stakeholders.
- Prioritized security investments: Rather than attempting to address every possible threat equally, NIST's risk-based approach helps organizations focus resources on controls that provide maximum risk reduction. This strategic prioritization often reduces security spending while improving protection through targeted investments in high-impact areas.
- Streamlined vendor management: Companies using NIST standards evaluate and manage third-party risks more effectively by requiring suppliers to demonstrate alignment. This approach to vendor assessment reduces vetting time, improves supply chain visibility, and creates accountability throughout the business ecosystem.
- Accelerated incident response: The structured incident response procedures outlined in the NIST cybersecurity framework enable organizations to detect, contain, and recover from breaches faster. Preestablished response playbooks, clear escalation paths, and defined recovery procedures reduce mean time to recovery (MTTR) and minimize business disruption during security incidents.
- Enhanced board confidence: NIST standards provide quantifiable metrics and maturity models that translate technical security risks into business language that executives understand. This clarity translates to more informed risk acceptance decisions, justifies security budget requests, and demonstrates due diligence to shareholders and regulators.
Challenges of implementing NIST frameworks
Despite the comprehensive nature and widespread acceptance, implementing NIST frameworks presents challenges for organizations of all sizes:
- Complexity: NIST publications are detailed and technical. Interpreting this guidance and applying it to a unique and diverse IT environment, which may include cloud infrastructure, on-premises systems, and operational technology, requires significant expertise.
- Resource constraints: A successful NIST implementation consumes resources, including a budget for security tools, time, and access to personnel with specialized cybersecurity skills. Many organizations have issues with balancing resource use with competing business priorities.
- Keeping pace with evolving standards: NIST regularly updates its frameworks to address emerging threats and technologies. Companies must continuously monitor changes and adjust their implementations to ensure their security is up to standard.
- Integration with existing programs: Most organizations have existing security programs. Harmonizing NIST's structured approach with these legacy systems can create friction and require significant effort to unify policies, tools, and workflows without creating visibility gaps.
- Need for continuous improvement: Maintaining NIST compliance requires ongoing assessment, metrics collection, and improvement processes that businesses can find challenging to maintain.
Actionable best practices for leveraging NIST standards
Navigating NIST integration challenges requires a strategic and methodical approach. These NIST implementation best practices help you move beyond checkbox compliance toward meaningful security improvements that align with recommended principles.
Understand the core NIST frameworks
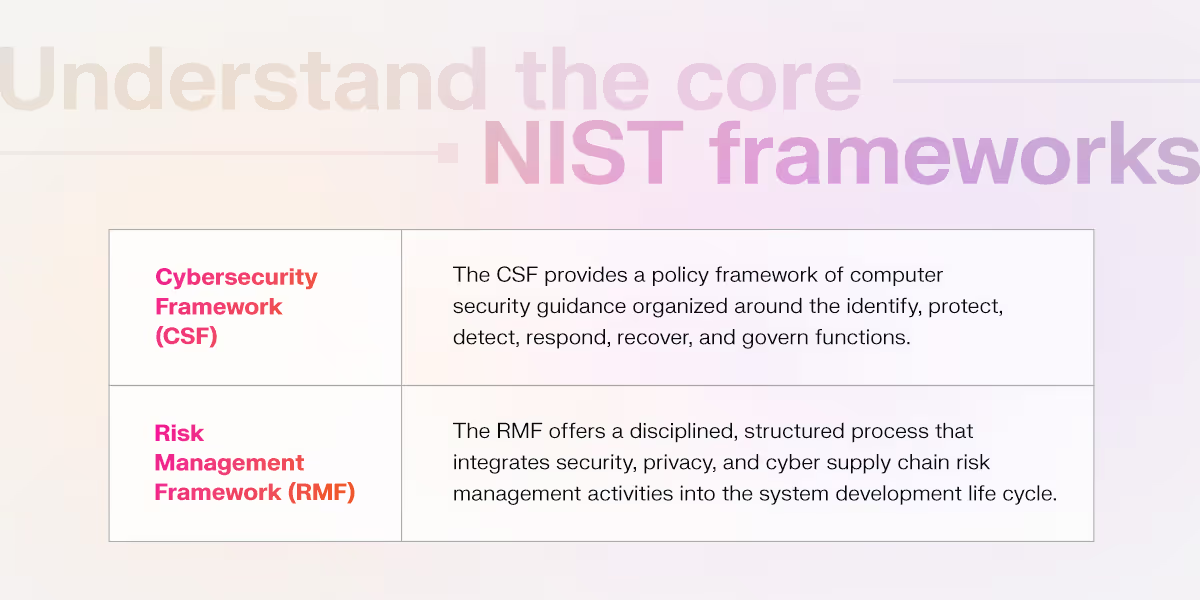
Before you can integrate NIST standards, you must understand the frameworks that define them. The core NIST frameworks that drive cybersecurity include:
- NIST Cybersecurity Framework (CSF): The CSF provides a policy framework of computer security guidance organized around the identify, protect, detect, respond, recover, and govern functions. This framework enables organizations to assess their current security posture, establish target states, and prioritize investments to manage cybersecurity risk effectively.
- NIST Risk Management Framework (RMF): The RMF offers a disciplined, structured process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. The RMF covers categorization, selection, implementation, assessment, authorization, and monitoring. This systematic approach ensures that security considerations are embedded throughout an organization's operations.
Assess current security posture
Conduct a comprehensive gap analysis comparing security controls against relevant NIST framework requirements. This assessment should examine technical controls, administrative processes, and physical security measures across all business functions. Organizations should document current capabilities using NIST's control families and implementation tiers to establish a baseline for improvement efforts.
Prioritize assessment findings based on risk exposure, regulatory requirements, and available resources. Focus initial efforts on high-impact controls that address critical vulnerabilities or compliance gaps. Third-party assessors familiar with NIST frameworks can also provide an objective evaluation and identify visibility gaps internal teams might miss.
Align security policies with framework guidelines
Map existing documentation to NIST frameworks, identifying areas requiring new policies or updates. Policies should define roles, responsibilities, and implementation expectations while remaining practical for daily operations.
Implementation guides should translate technical NIST language into specific instructions relevant to different stakeholder groups. Create templates and standard operating procedures that embed NIST principles into routine activities. Establish governance structures that ensure policy adherence while providing flexibility for legitimate business needs.
Apply comprehensive security controls
Implement technical, administrative, and physical controls incrementally, following NIST's defense-in-depth philosophy. Technical controls should address network security, access management, encryption, and system hardening based on NIST configuration baselines. Administrative controls must encompass personnel security, training programs, incident response procedures, and vendor management practices. Physical controls protect facilities, equipment, and media according to NIST guidelines for environmental protection and access restrictions.
Use NIST's control baselines as starting points, then adjust based on risk assessments and business requirements. Document control implementation details, including configuration settings, responsible parties, and testing procedures.
Leverage automation tools
Deploy technology solutions that streamline NIST compliance activities and reduce manual effort. Security orchestration platforms can automate control assessment, evidence collection, and reporting processes. Continuous monitoring tools provide real-time visibility into control effectiveness and compliance status. Governance, risk, and compliance (GRC) platforms centralize NIST framework management, tracking implementation progress and maintaining documentation.
Integration between security tools enables comprehensive coverage of NIST requirements while minimizing operational overhead. Solutions that map directly to NIST frameworks provide prebuilt templates and assessment workflows.
Build organizational NIST expertise
Develop internal capabilities through targeted education programs that address different stakeholder needs. NIST champions within different departments translate framework requirements into business-relevant terms.
Provide ongoing training that addresses framework updates, emerging threats, and lessons learned from implementations. Professional certificates validate NIST expertise and demonstrate organizational commitment to standards-based security. Create knowledge repositories that capture implementation experiences, common challenges, and successful solutions for future reference.
Regularly review and update controls
Ongoing review cycles evaluate control effectiveness, identify improvement opportunities, and incorporate framework updates. Use these routine risk assessments to inform control adjustments and resource allocation decisions. Incident response activities must include root cause analysis that examines NIST control failures and enhancement opportunities.
Participation in NIST comment periods and industry working groups helps you influence framework development and learn from peer experiences. Benchmark implementation practices against industry leaders and incorporate successful strategies. Establish feedback mechanisms that enable all stakeholders to contribute improvement suggestions based on operational experience.
Discover more about NIST with Darktrace
NIST frameworks provide essential structure for building robust cybersecurity programs, though implementation requires careful planning and sustained commitment. Organizations leveraging NIST standards achieve improved security posture, risk management, and regulatory compliance.
Darktrace's AI-driven security platform aligns with the NIST cybersecurity framework with automated threat detection and response capabilities that support the Detect and Respond functions. Download our white paper on resource mapping or explore our blog for additional resources about implementing NIST guidelines.



























