Introduction: Cloud investigations
In cloud security, speed, automation and clarity are everything. However, for many SOC teams, responding to incidents in the cloud is often very difficult especially when attackers move fast, infrastructure is ephemeral, and forensic skills are scarce.
In this blog we will walk through an example that shows exactly how Darktrace Cloud Detection and Response (CDR) and automated cloud forensics together, solve these challenges, automating cloud detection, and deep forensic investigation in a way that’s fast, scalable, and deeply insightful.
The Problem: Cloud incidents are hard to investigate
Security teams often face three major hurdles when investigating cloud detections:
Lack of forensic expertise: Most SOCs and security teams aren’t natively staffed with forensics specialists.
Ephemeral infrastructure: Cloud assets spin up and down quickly, leaving little time to capture evidence.
Lack of existing automation: Gathering forensic-level data often requires manual effort and leaves teams scrambling around during incidents — accessing logs, snapshots, and system states before they disappear. This process is slow and often blocked by permissions, tooling gaps, or lack of visibility.
How Darktrace augments cloud investigations
1. Darktrace’s CDR finds anomalous activity in the cloud
An alert is generated for a large outbound data transfer from an externally facing EC2 instance to a rare external endpoint. It’s anomalous, unexpected, and potentially serious.
2. AI-led investigation stitches together the incident for a SOC analyst to look into
When a security incident unfolds, Darktrace’s Cyber AI Analyst TM is the first to surface it, automatically correlating behaviors, surfacing anomalies, and presenting a cohesive incident summary. It’s fast, detailed, and invaluable.
Once the incident is created, more questions are raised.
- How were the impacted resources compromised?
- How did the attack unfold over time – what tools and malware were used?
- What data was accessed and exfiltrated?
What you’ll see as a SOC analyst: The incident begins in Darktrace’s Threat Visualizer, where a Cyber AI Analyst incident has been generated automatically highlighting large anomalous data transfer to a suspicious external IP. This isn’t just another alert, it’s a high-fidelity signal backed by Darktrace’s Self-Learning AI.
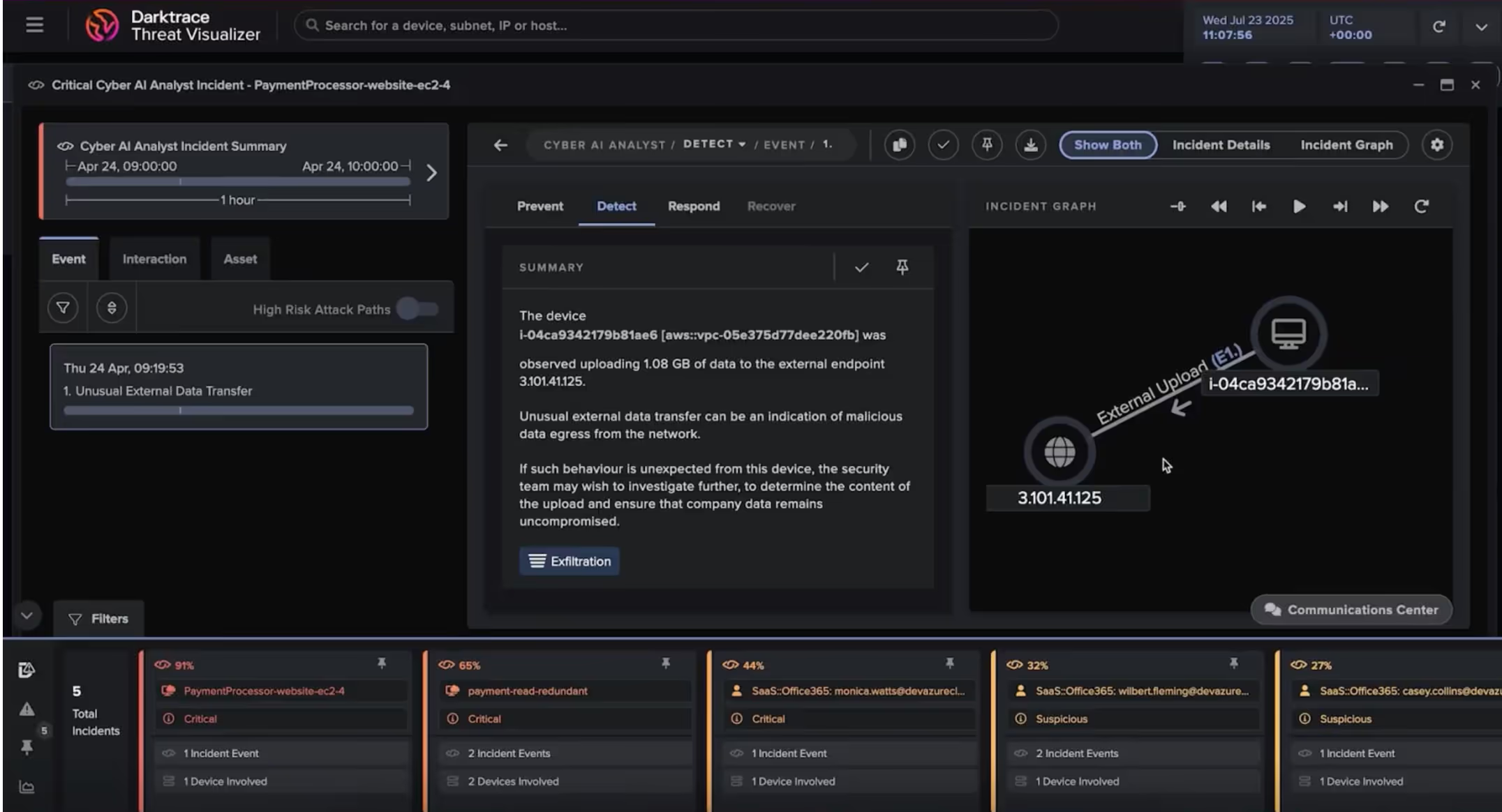
The analyst can then immediately pivot to Darktrace / CLOUD’s architecture view (see below), gaining context on the asset’s environment, ingress/egress points, connected systems, potential attack paths and whether there are any current misconfigurations detected on the asset.
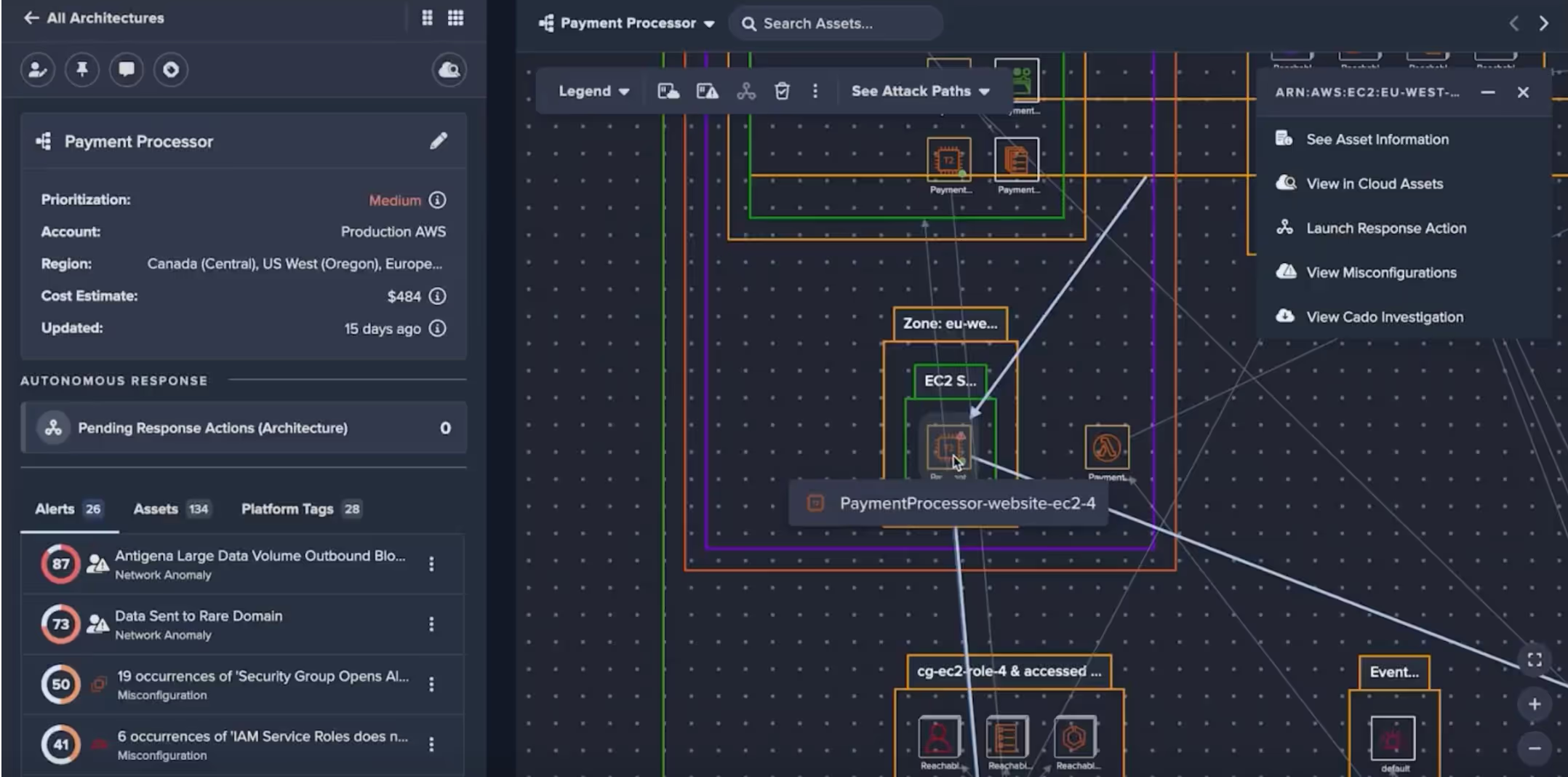
3. Automated forensic capture — No expertise required
Then comes the game-changer, Darktrace’s recent acquisition of Cado enhances its cloud forensics capabilities. From the first alert triggered, Darktrace has already kicked in and automatically processed and analyzed a full volume capture of the EC2. Everything, past and present, is preserved. No need for manual snapshots, CLI commands, or specialist intervention.
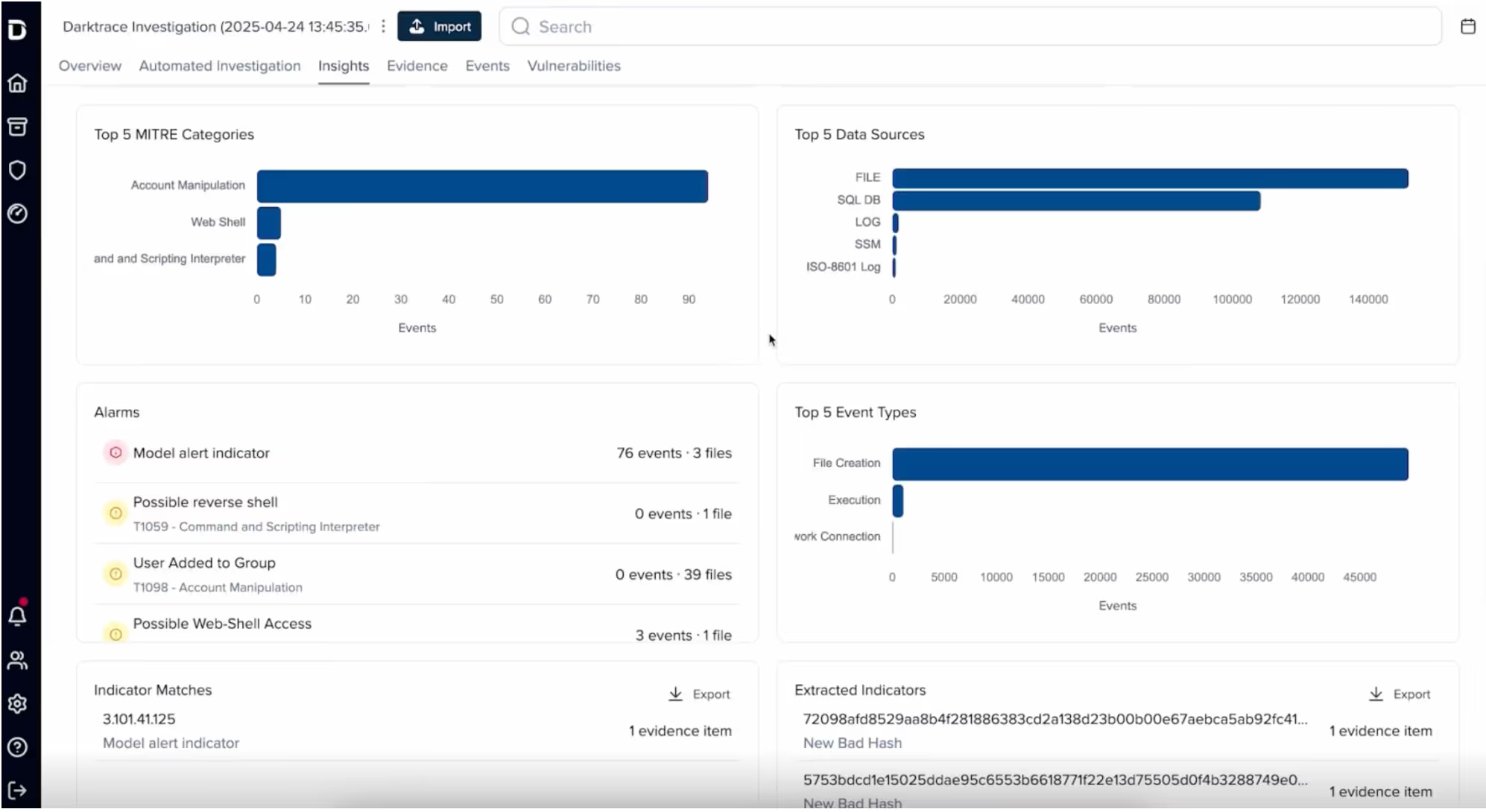
Darktrace then provides a clear timeline highlighting the evidence and preserving it. In our example we identify:
- A brute-force attempt on a file management app, followed by a successful login
- A reverse shell used to gain unauthorized remote access to the EC2
- A reverse TCP connection to the same suspicious IP flagged by Darktrace
- Attacker commands showing how the data was split and prepared for exfiltration
- A file (a.tar) created from two sensitive archives: product_plans.zip and research_data.zip
All of this is surfaced through the timeline view, ranked by significance using machine learning. The analyst can pivot through time, correlate events, and build a complete picture of the attack — without needing cloud forensics expertise.
Darktrace even gives the ability to:
- Download and inspect gathered files in full detail, enabling teams to verify exactly what data was accessed or exfiltrated.
- Interact with the file system as if it were live, allowing investigators to explore directories, uncover hidden artifacts, and understand attacker movement with precision.



Why this matters?
This workflow solves the hardest parts of cloud investigation:
- Capturing evidence before it disappears
- Understanding attacker behavior in detail - automatically
- Linking detections to impact with full incident visibility
This kind of insight is invaluable for organizations especially regulated industries, where knowing exactly what data was affected is critical for compliance and reporting. It’s also a powerful tool for detecting insider threats, not just external attackers.
Darktrace / CLOUD and Cado together acts as a force multiplier helping with:
- Reducing investigation time from hours to minutes
- Preserving ephemeral evidence automatically
- Empowering analysts with forensic-level visibility
Cloud threats aren’t slowing down. Your response shouldn’t either. Darktrace / CLOUD + Cado gives your SOC the tools to detect, contain, and investigate cloud incidents — automatically, accurately, and at scale.
[related-resource]
Secure your cloud with confidence
Learn how Darktrace delivers autonomous detection, investigation, and response across multi-cloud and SaaS environments.
.avif)








































