Introduction
In today's digital landscape, cybercriminals are constantly devising new and innovative ways to infiltrate and compromise corporate systems. One such tactic is called typosquatting: the registration of domains that closely resemble a real organization in order to trick users into visiting a fraudulent website. Before any damage could be done, researchers at Cado Security Labs (now part of Darktrace) recently discovered a domain that bore a striking resemblance to the Cado corporate domain during a routine check. In this blog, we will discuss how this domain was identified, and the steps taken following discovery.
Look and you shall find
Monitoring for spoofed domains is a function that helps a threat intel team detect malicious actors preparing their infrastructure for their campaigns. This early detection can prevent potential attacks and protect an organization's reputation and assets from harm.
At Cado Security (now Darktrace), this issue is proactively addressed using a tool called “ dnstwist “ - a powerful domain generation and lookup tool that helps identify domains that could be used as part of phishing attacks. For example, using the corporate domain, cadosecurity.com, dnstwist generated nearly 9,000 permutations of the Cado domain and attempted DNS resolutions of them.
Not if, but when..
During a routine check, Cado discovered that just three days prior, a domain had been registered that contained a character substitution similar to what is seen for typosquatting attacks, highlighting that a potential threat was emerging.
Typosquatting attacks are typically done by deliberately including typos, numbers, or symbols in the domain name that a user might accidentally type or with a quick glance might consider to be legitimate. This might involve adding an extra character, such as "Cadosecurityy.com," or replacing a letter with a similar-looking number or symbol, like "Cado5ecurity.com" or "Cad0security.com" (using a zero instead of the letter 'O'). Another variation of typosquatting is the homoglyph or homograph attack, which uses characters (or glyphs) from other scripts that are very visually similar to register domains that may fool a user. For example, using Cyrillic characters mixed with Latin characters, an attacker might create a domain like "Сadosecurity.com," where the 'C' is replaced with its Cyrillic counterpart, which looks almost identical.
Once this domain was identified, it was quickly discovered that connections to the malicious domain were being redirected to Cado’s legitimate domain. This redirection indicates that the threat actor behind this activity was likely intending to imitate the domain, potentially as part of a future phishing attack.
Upon further investigation, Cado found that this malicious domain was registered through “Apiname” and resolved to IP address 94[.]154[.]35[.]15. Open Source Intelligence analysis revealed that not only was the domain being mimicked, but also several other tech companies' domains have been targeted in a similar fashion. This suggests that it was created as part of a broader campaign to target a large number of brands. Where possible, the affected companies were notified prior to this blog being released.
The threat actor also created an X (formerlyTwitter) account as Cado with the typo’d domain mimicking our own X account and in one instance, they had taken it as far as purchasing a Gold Checkmark, adding followers, and following people related to Cado, in order to create a sense of authenticity.
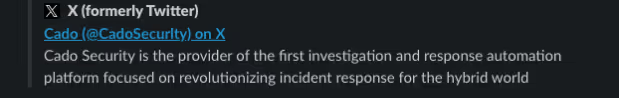
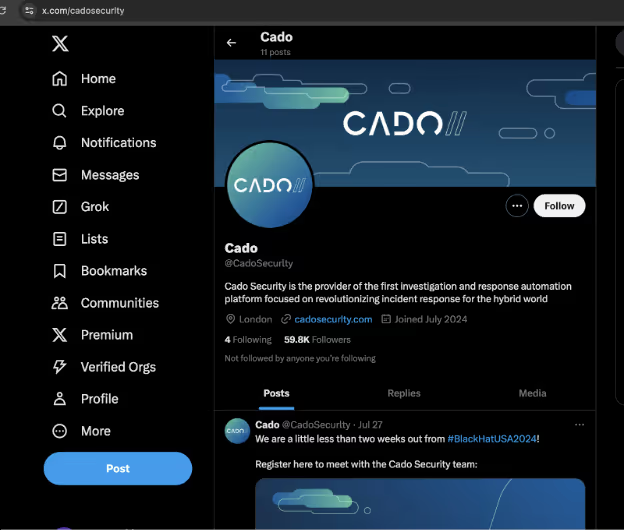
As seen with the other tech related companies that were also victims of the same domain registration typo activity, Cado found the threat actor had also created X accounts for some of those companies as well.
Actions speak louder than words
When Cado identified that the malicious domain was redirecting to its website, the following proactive actions were taken:
- Informed all staff about the current situation and reminded them of the actions they should take. Fostering a security-conscious culture where everyone plays their part in defending against cyber threats is key for a business’ cyber security posture. Ensure your cyber security training is always updated to reflect the latest threats, and that staff are briefed on a routine basis. By investing time and resources into employee cybersecurity education, businesses can significantly reduce the risk of a breach, protect sensitive information, and maintain smooth operations.
- Searched for any emails originating from the malicious domain, and implemented alerting and a block for future emails. By doing so, threat actors were unable to send malicious content or phishing attempts to staff inboxes. This step not only protects team members, but also limits the potential damage caused by any malicious emails.
- Reported the activity to the DNS registrar who subsequently suspended the domain. By taking this action, not only was the issue addressed at hand, but it also contributed to the overall security of the internet by having a potentially malicious domain taken offline.
Additional typosquatting domains identified
Where possible the organizations included below have all been alerted regarding these fraudulent domains.
URLs
- biaizetech[.]com
- cadosecurlty[.]com
- changeliy[.]com
- ciickup[.]com
- elliptlc[.]com
- miikroad[.]com
- ogiivy[.]com
- q0nt0[.]com
- raiiwayapp[.]com
- scrlb3[.]com
- sh0rtcut[.]com
- slgmaprime[.]com
- slnglegrain[.]com
- spndesk[.]com
- twinmotlon[.]com
- tlnulti[.]com
- 0penraven[.]com
IP addresses
94[.]154[.]35[.]15
The key takeaway
This discovery underscores the importance of staying vigilant and proactive in protecting against such potential threats. It also highlights the need to monitor domain registrations, especially those that closely resemble our own, as well as staying abreast of the latest cybersecurity trends and best practices. By being aware of these potential risks and taking adequate measures to secure our domains, teams can collectively work towards mitigating the impact of such activities on organizations and the broader tech industry.













































![Pivoting off the previous event by filtering the timeline to events within the same window using timestamp: [“2026-02-18T09:09:00Z” TO “2026-02-18T09:12:00Z”].](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/69a8a18526ca3e653316a596_Screenshot%202026-03-04%20at%201.17.50%E2%80%AFPM.png)

