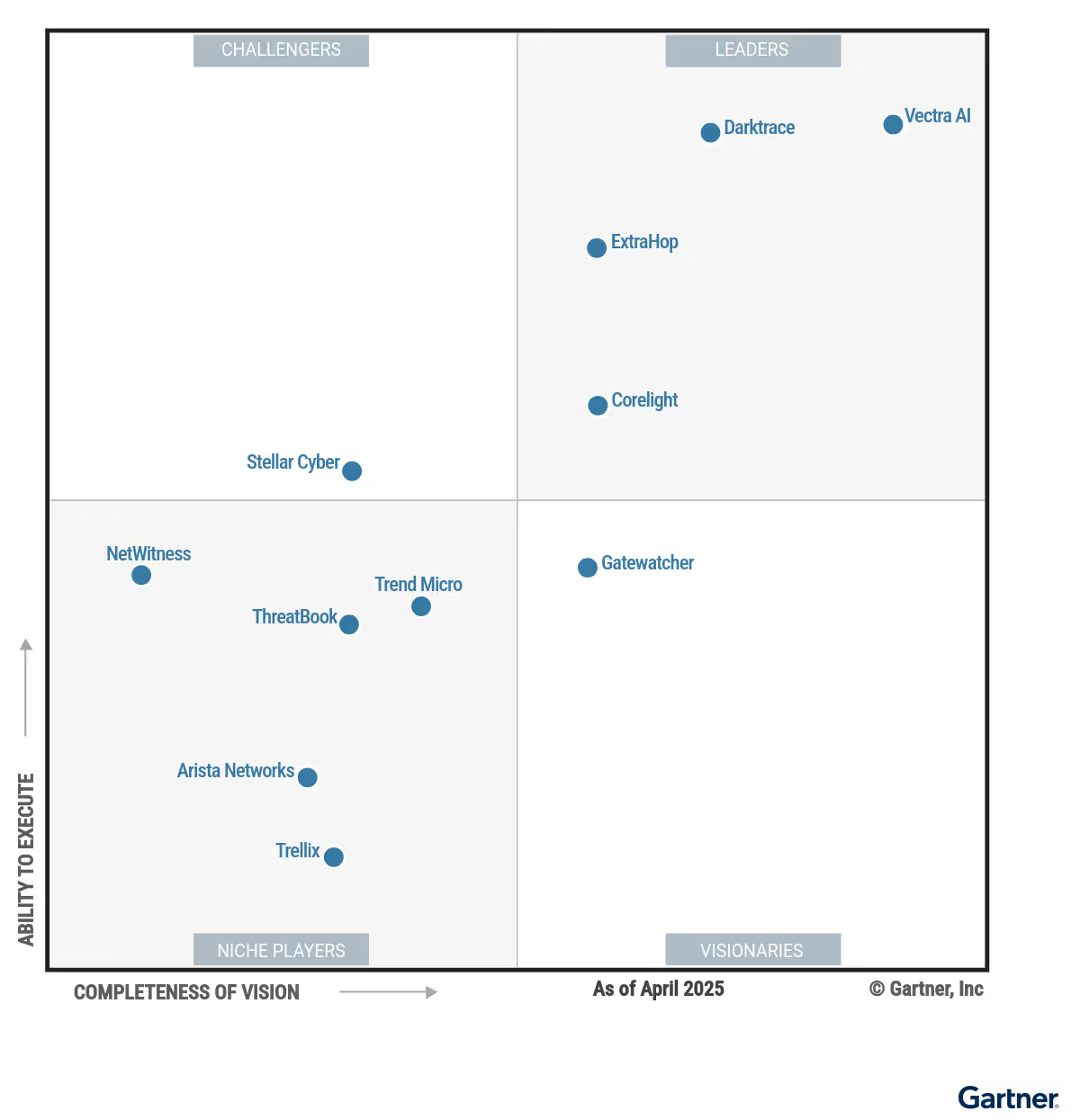
Darktrace has been recognized as a Leader in the first ever Magic Quadrant™ for Network Detection and Response (NDR).
A Gartner Magic Quadrant is a culmination of research in a specific market, giving you a wide-angle view of the relative positions of the market’s competitors. CIOs and CISOs can use this research to make informed decisions about NDR, which is evolving to offer broader threat detection. We encourage our customers to read the full report to get the complete picture.
Darktrace has also received accolades in other recent NDR leadership evaluations including IDC named as market share leader, and KuppingerCole’s heralding us as an Overall Leader, Product Leader, Market Leader and Innovation Leader. We believe we have continued to be identified as a Leader due to the strength of our capabilities in NDR, driven by our unique application of AI in cybersecurity, continuous product innovation, and our ability to execute on a global scale to meet the evolving needs of our customers.
We’re proud of Darktrace’s unrivaled market, and ability to execute effectively in the network security market, reflecting our commitment to delivering high-quality, reliable solutions that meet the evolving needs of our customers.
Why is Darktrace the market share leader and undisputed force in NDR?
Transforming network security and shifting to an AI-led SOC
Darktrace’s Self-Learning AITM understands normal for your entire network, intelligently detecting anomalies and containing sophisticated threats without historical attack data. This approach, based on advanced, unsupervised machine learning, enables Darktrace to catch novel, unknown and insider threats that traditional tools miss and other NDR vendors can’t detect. Darktrace has identified and contained attempted exploits of zero-day vulnerabilities up to 11 days before public disclosure.
We change SOC dynamics with our Cyber AI AnalystTM, which eliminates manual triage and investigation by contextualizing all relevant alerts across your environment, including third-party alerts, and performing end-to-end investigations at machine speed. Cyber AI Analyst gives your team the equivalent of 30 extra full time Level 2 analysts without the hiring overhead2, so you can shift your team away from manual, reactive workflows and uplift them to focus on more proactive tasks.
When combined, Darktrace Self-Learning AI and Cyber AI Analyst go far beyond the capabilities of traditional NDR approaches to completely transform your network security and help your teams operate at the speed and scale of AI.
Coverage across the extended IT enterprise and all-important OT devices
We believe the report validates the business-centric approach that Darktrace uses to deploy AI locally and train it solely on each unique environment, giving our customers tailored security outcomes without compromising on privacy.
This contrasts with other NDR vendors that require cloud connectivity to either deliver full functionality or to regularly update their globally trained models with the latest attack data. This capability is particularly sought after by organizations who are no longer just on-premise, have operational technology (OT) networks, or those that operate in classified environments.
Darktrace serves these organizations and industries by extending IT and unifying OT security within a single solution, reducing alert fatigue and accelerating alert investigation in industrial environments.
With Darktrace / NETWORK you can achieve:
- Full visibility across your modern network, including on-premises, virtual networks, hybrid cloud, identities, remote workers and OT devices
- Precision threat detection across your modern network to identify known, unknown and insider threats in real-time without relying on rules, signatures or threat intelligence,
- 10x accelerated incident response times with agentic AI that uplifts your team and enables them to focus on more proactive tasks
- Containment of threats with the first autonomous response solution proven to work in the enterprise, stopping attacks from progressing at the earliest stages with precise actions that avoid business disruption
Going beyond traditional NDR to build proactive network resilience
Darktrace does not just stop at threat detection, it helps you prevent threats from occurring and increase your resiliency for when attacks do happen. We help discover and prioritize up to 50% more risks across your environment and optimize incident response processes, reducing the impact of active cyber-attacks using an understanding of your data.
Attack path modeling: By leveraging attack path modeling and AI-driven risk validation, customers can close gaps before they’re exploited, focusing resources where they’ll have the greatest impact.
AI-driven playbooks and breach simulations: With AI-driven playbooks and realistic breach simulations, Darktrace helps your team practice response, strengthen processes, and reduce the impact of real-world incidents. You’re not just reacting; you’re proactively building long-term resilience.
Continued innovation in network security
Darktrace leads innovation in the NDR market with more than 200+ patents and active filings, covering a range of detection, response and AI techniques. Our AI Research Center is foundational to our ongoing innovation, including hundreds of R&D employees examining how AI can be applied to real-world problems and augment human teams.
Trusted by thousands of customers globally
Our commitment to innovation and patented Self-Learning AITM has protected organizations in all industries from known and novel attacks since 2013, bolstering network security and augmenting human teams for our 10,000 active customers across 110 countries. These organizations place a great deal of trust in Darktrace’s unique approach to cybersecurity and application of AI to detect and respond to threats across their modern network.
A new standard for NDR
Darktrace / NETWORK is not just another NDR tool; we are the most advanced network security platform in the industry that pushes beyond traditional capabilities to protect thousands of organizations against known and novel threats.
From real-time threat detection and autonomous response to proactive risk management, we’re transforming network security from reactive to resilient.
[related-resource]
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
References
1, 3 Gartner, Magic Quadrant for Network Detection and Response, by Thomas Lintemuth, Esraa ElTahawy, John Collins, Charanpal Bhogal, 29 May, 2025
2 Darktrace Cyber AI Analyst fleet data, 2023
Download your copy today
Read the Gartner® Magic Quadrant™ report & discover what it means to be recognized in NDR as a leader.
.avif)
























![Pivoting off the previous event by filtering the timeline to events within the same window using timestamp: [“2026-02-18T09:09:00Z” TO “2026-02-18T09:12:00Z”].](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/69a8a18526ca3e653316a596_Screenshot%202026-03-04%20at%201.17.50%E2%80%AFPM.png)

